6 - 24 WiNG 5.6 Access Point System Reference Guide
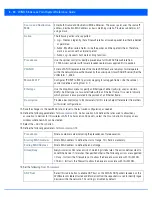
WEP 128 and Keyguard Deployment Considerations
WEP 128 and KeyGuard
Before defining a WEP 128 supported configuration on a WLAN, refer to the following deployment guidelines to ensure the
configuration is optimally effective:
• Motorola Solutions recommends additional layers of security (beyond WEP) be enabled to minimize the likelihood of data
loss and security breaches. WEP enabled WLANs should be mapped to an isolated VLAN with Firewall policies restricting
access to hosts and suspicious network applications.
• WEP enabled WLANs should only be permitted access to resources required by legacy devices.
• KeyGuard is not supported on AP6511 model access points.
• If WEP support is needed for WLAN legacy device support, 802.1X EAP authentication should be also configured in order
for the WLAN to provide authentication and dynamic key derivation and rotation.
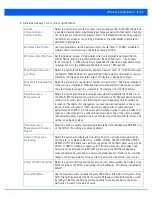
6.1.3 Configuring WLAN Firewall Support
Wireless LANs
A Firewall is a mechanism enforcing access control, and is considered a first line of defense in protecting proprietary
information within an access point managed WLAN. The means by which this is accomplished varies, but in principle, a Firewall
is a mechanism that blocks and permits data traffic. For a Firewall overview, see
Wireless Firewall on page 8-2
.
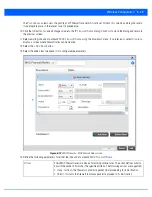
WLANs use Firewalls like
Access Control Lists
(ACLs) to filter/mark packets based on the WLAN from which they arrive, as
opposed to filtering packets on Layer 2 ports. An ACL contains an ordered list of
Access Control Entries
(ACEs). Each ACE
specifies an action and a set of conditions (rules) a packet must satisfy to match the ACE. The order of conditions in the list is
critical because the access point stops testing conditions after the first match.
IP based Firewall rules are specific to source and destination IP addresses and the unique rules and precedence orders
assigned. Both IP and non-IP traffic on the same Layer 2 interface can be filtered by applying both an IP ACL and a MAC.
A MAC Firewall rule uses source and destination MAC addresses for matching operations, where the result is a typical
allow
,
deny
or
mark
designation to WLAN packet traffic.
Keep in mind, IP and non-IP traffic on the same Layer 2 interface can be filtered by applying both an IP ACL and a MAC ACL to
the interface.
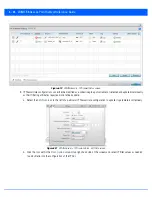
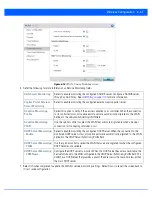
To review existing Firewall configurations, create a new Firewall configuration or edit the properties of a WLAN’s existing
Firewall:
1. Select the
Configuration
tab from the Web UI.
2. Select
Wireless.
3. Select
Wireless LANs
to display a high level display of existing WLANs.
4. Select the
Add
button to create a new WLAN or
Edit
to modify the properties of an existing wireless controller WLAN.
5. Select
Firewall
from the WLAN options.
Summary of Contents for WiNG 5.6
Page 1: ...Motorola Solutions WiNG 5 6 ACCESS POINT SYSTEM REFERENCE GUIDE ...
Page 2: ......
Page 22: ...8 WiNG 5 6 Access Point System Reference Guide ...
Page 26: ...1 4 WiNG 5 6 Access Point System Reference Guide ...
Page 38: ...2 12 WiNG 5 6 Access Point System Reference Guide ...
Page 74: ...3 36 WiNG 5 6 Access Point System Reference Guide ...
Page 468: ...6 2 WiNG 5 6 Access Point System Reference Guide Figure 6 1 Configuration Wireless menu ...
Page 568: ...6 102 WiNG 5 6 Access Point System Reference Guide ...
Page 614: ...7 46 WiNG 5 6 Access Point System Reference Guide ...
Page 660: ...8 46 WiNG 5 6 Access Point System Reference Guide ...
Page 716: ...9 56 WiNG 5 6 Access Point System Reference Guide ...
Page 730: ...10 14 WiNG 5 6 Access Point System Reference Guide ...
Page 982: ...14 20 WiNG 5 6 Access Point System Reference Guide ...
Page 984: ...A 2 WiNG 5 6 Access Point System Reference Guide ...
Page 1046: ...B 62 WiNG 5 6 Access Point System Reference Guide ...
Page 1047: ......