SECTION 3
CONFIGURATION
3-8
SECTION 3, CONFIGURATION
Field Description
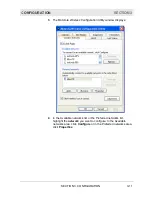
Network
Authentication
Select if your access point requires
Authentication. The option selected here
must match the Authentication type used by
the AP. The options are:
Open
System
The Open System
Authentication method is
used, meaning the AP you
are trying to associate with
will not verify the
identification your unit.
Shared The
Shared
(PSK)
authentication method is
used. You need to share
the same key between
your AP and client.
WPA Wi-Fi
®
Protected Access
(WPA) authentication
(802.1X) is used with an
EAP type.
WPA-PSK WPA
authentication
(802.1X) is used with a
pre-shared key.
Motorola recommends using WPA-PSK
because it provides the strongest security
algorithm.
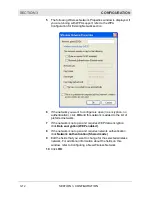
Data encryption
Select the type of security encryption
algorithm used on this network. The
security setting encrypts your wireless
transmission.
WEP
Wired Equivalent Privacy
TKIP
Temporal Key Integrity
Protocol - changes the
temporal key often (provides
1 Key)
AES Advanced
Encryption
Standard (provides 1 Key)
Motorola recommends using AES because
it provides the strongest security algorithm.