AirWorks AWK-3131-RCC
Web Console Configuration
3-28
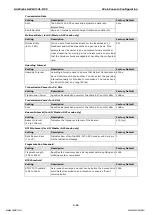
Port cost
Setting
Description
Factory Default
Enable/ Disable
Input a higher cost to indicate that this port is less suitable as a
node for the Spanning Tree topology
2000000
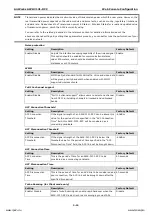
Edge port
Setting
Description
Factory Default
Checked/ unchecked
Sets a port, which no BPDU expectedly goes through, as an
edge port
unchecked, except
AP port
NOTE
We recommend you set an edge port for the port, which is connected to a non-STP/RSTP sub-network or an
end device (PLC, RTU, etc.) as opposed to network equipment. This can prevent unnecessary waiting and
negotiation of STP/RSTP protocol, and accelerate system initialization. When an edge port receives BPDUs, it
can still function as an STP/RSTP port and start negotiation.
Setting an edge port is different from disabling STP/RSTP on a port. If you disable STP/RSTP, a port will not
deal with STP/RSTP BPDUs at all.
Port Status
Port Status indicates the current Spanning Tree status of this port. Use Forwarding for normal transmission,
or Blocking to block transmission.
SNMP Agent
The AWK-3131-RCC supports SNMP V1/V2c/V3. SNMP V1 and SNMP V2c use a community string match for
authentication, which means that SNMP servers access all objects with read-only or read/write permissions
using the community string public/private (default value). SNMP V3, which requires you to select an
authentication level of MD5 or SHA, is the most secure protocol. You can also enable data encryption to
enhance data security.
The AWK-3131-RCC’s MIB can be found in the software CD and supports reading the attributes via SNMP. (Only
get method is supported.)
SNMP security modes and security levels supported by the AWK-3131-RCC are shown in the following table.
Select the security mode and level that will be used to communicate between the SNMP agent and manager.
Protocol
Version
Setting on
UI web page
Authentication
Type
Data
Encryption
Method
SNMP
V1, V2c
V1, V2c
Read
Community
Community string No
Use a community string match for
authentication
V1, V2c
Write/Read
Community
Community string No
Use a community string match for
authentication
SNMP V3 No-Auth
No
No
Use account with admin or user to access
objects
MD5 or SHA
Authentication
based on MD5 or
SHA
No
Provides authentication based on HMAC-MD5,
or HMAC-SHA algorithms. 8-character
passwords are the minimum requirement for
authentication.
MD5 or SHA
Authentication
based on MD5 or
SHA
Data
encryption
key
Provides authentication based on HMAC-MD5
or HMAC-SHA algorithms, and data encryption
key. 8-character passwords and a data
encryption key are the minimum requirements
for authentication and encryption.
www.ipc2u.ru
www.moxa.pro