TAP-125-U-W-X-Z
(YYYYYYYY)
Web Console Configuration
3-20
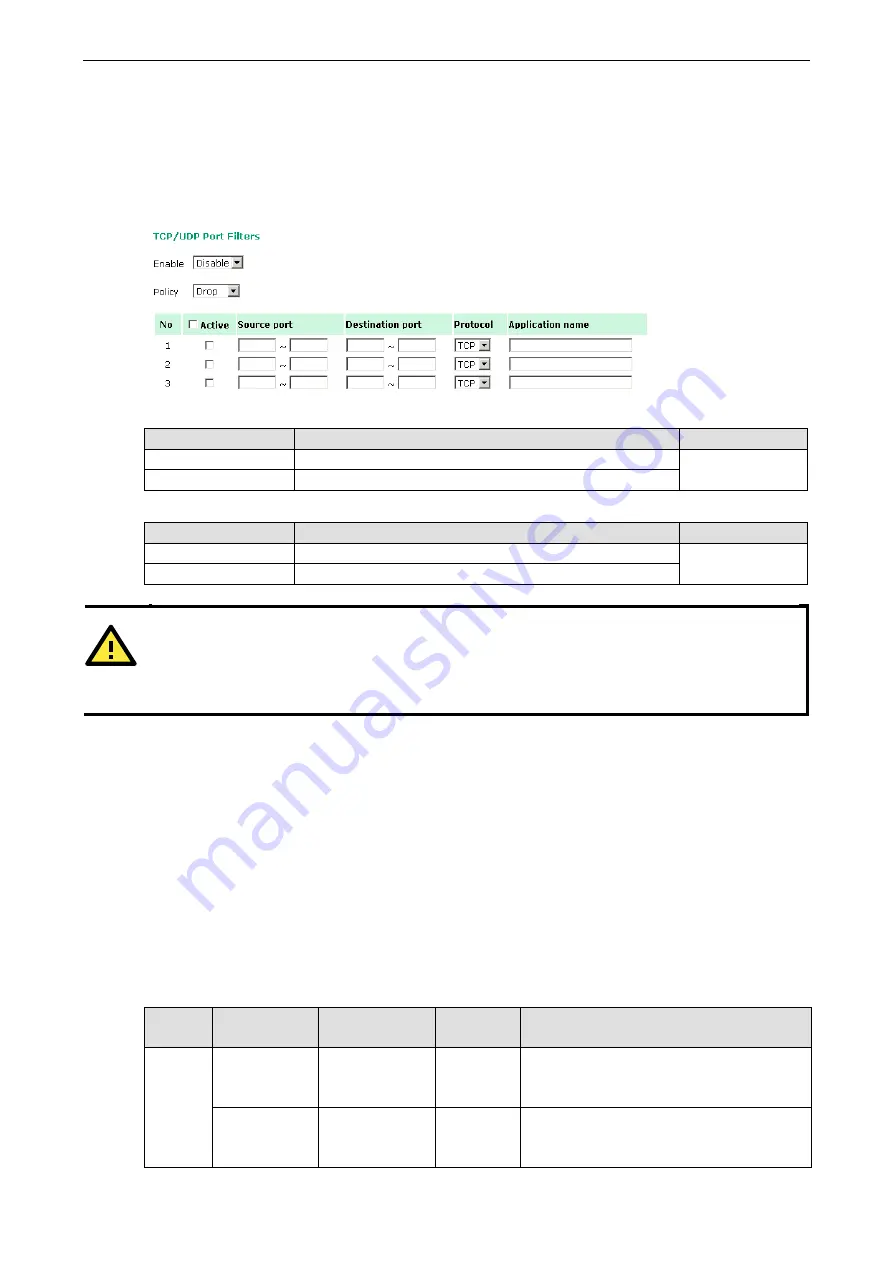
The TAP-125-U-W-X-Z (YYYYYYYY) provides 8 entities for setting the range of source/destination ports of a
specific protocol. In addition to selecting TCP or UDP protocol, you can set either the source port, destination
port, or both. The end port can be left empty if only a single port is specified. Of course, the end port cannot be
larger than the start port.
The Application name is a text string that describes the corresponding entity with up to 31 characters.
Remember to check the Active check box for each entity to activate the setting.
Enable
Setting
Description
Factory Default
Enable
Enables TCP/UDP port filter
Disable
Disable
Disables TCP/UDP port filter
Policy
Setting
Description
Factory Default
Accept
Only the packets fitting the entities on list can be allowed.
Drop
Drop
Any packet fitting the entities on list will be denied.
SNMP Agent
The TAP-125-U-W-X-Z (YYYYYYYY) supports SNMP V1/V2c/V3. SNMP V1 and SNMP V2c use a community string
match for authentication, which means that SNMP servers access all objects with read-only or read/write
permissions using the community string public/private (default value). SNMP V3, which requires you to select
an authentication level of MD5 or SHA, is the most secure protocol. You can also enable data encryption to
enhance data security.
The TAP-125-U-W-X-Z (YYYYYYYY)’s MIB can be found in the software CD and supports reading the attributes
via SNMP. (Only get method is supported.)
SNMP security modes and security levels supported by the TAP-125-U-W-X-Z (YYYYYYYY) are shown in the
following table. Select the security mode and level that will be used to communicate between the SNMP
agent and manager.
Protocol
Version
Setting on
UI web page
Authentication
Type
Data
Encryption
Method
SNMP
V1, V2c
V1, V2c
Read
Community
Community string No
Use a community string match for
authentication
V1, V2c
Write/Read
Community
Community string No
Use a community string match for
authentication
ATTENTION
Be careful when you enable the filter function:
Drop + “
no
entity on list is activated” = all packets are allowed
Accept + “
no
entity on list is activated” = all packets are denied
















































