Chapter 3 – RouteFinder Software Operation
Multi-Tech RouteFinder RF650VPN User Guide
52
Microsoft IAS
The following section describes the settings for Microsoft’s IAS (Radius server for MS Windows NT and
2000). If you have a different Radius server, you need the following information to use RouteFinder’s user
authentication.
The Radius receives a request with three data fields:
·
User name
·
Password in clear text (PAP)
·
Type of proxy (string HTTP or SOCKS) in the NAS Identifier field
Based on this information, your RADIUS server should decide whether or not to grant access to the
proxy, and send back an answer packet.
Configuring Microsoft’s IAS Radius Server
IAS is delivered with all versions of Microsoft Windows 2000 Server, but is generally not installed by
default. For Microsoft Windows NT4, IAS is a component of the NT4 Option Pack and is available
without extra charge. The MS Windows NT4 IAS version has fewer features than the 2000 version, but it
is quite sufficient for the usual authentication settings of the RouteFinder.
1.
Check whether the IAS service is installed. If it is not, install it.
2.
Create a user group for every proxy that is to be used.
Note: Name the group according to the appropriate proxy service. For example, the name for the
HTTP proxy could be called HTTP proxy users. Now assign all those users that are to be able to use
the appropriate service to this group.
3.
Activate the user flag Allow dial-in-access to the network of every user in these groups.
This setting is found in the user properties. MS Windows NT/2000 uses this as the “master flag” to
allow any kind of network remote access.
4.
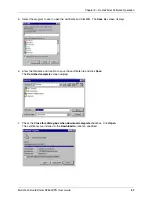
Open the administration program for the IAS service.
5.
Add a client. This requires the following information:
Any client name: Enter the DNS name of your RouteFinder system here.
Protocol: Choose Radius.
IP address of the client: this is the internal IP address of your RouteFinder system.
Client Vendor: Enter Radius Standard.
A shared secret: enter any password. You will need this password later to configure the Radius
server with the configuration tool WebAdmin.
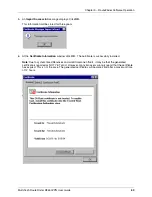
6.
Open the RAS Rules menu. A standard rule is entered here. If you intend to only use IAS for the
RouteFinder, you can delete this entry. Enter a rule for every proxy. Choose the name appropriately
(e.g., HTTP access). Add two conditions:
Condition 1: The NAS-Identifier field must correspond to a string according to the following table:
Proxy-type
NAS identifier corresponds to string
HTTP
HTTP
SOCKS SOCKS
Condition 2: the Windows group of the accessing user must correspond to the user group
established in step 2. The access is only granted if both conditions are met by the user.
7.
Edit the profile of the guideline by allowing unencrypted authentication (PAP). Leave the values of
the other dialog pages unchanged.