|
Function Specification
73
3.3.16.
Statistics
The detection status of this product's security/scan function can be confirmed through statistical information.
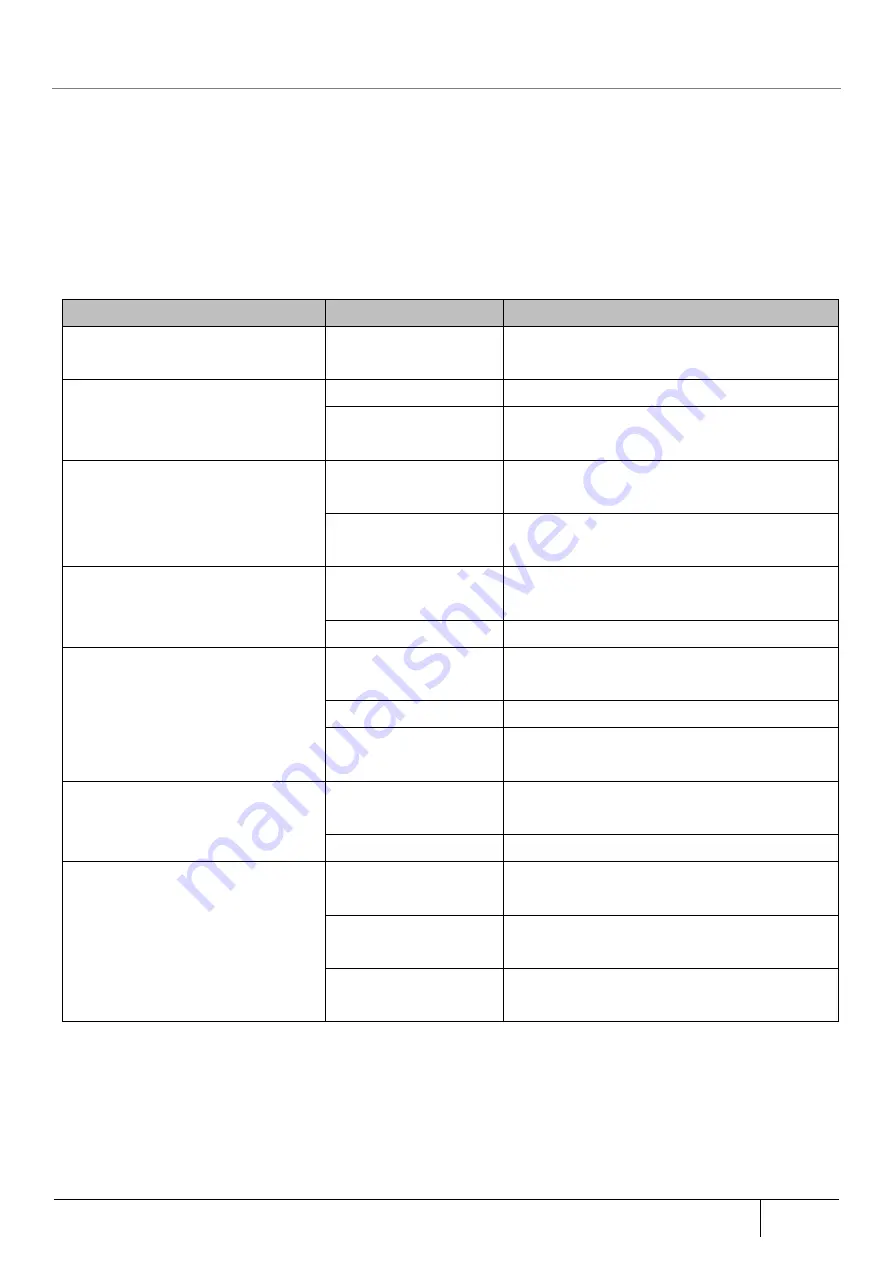
[Statistical information contents]
The number of packets intercepted and scanned items of each FW/AV/IPS/WG/UF/KF/APG function.
When logging only the operation setting at the threat detection of each function of AV/IPS/WG/UF/KF/APG, the
scanned value is counted.
Statistical information can be viewed daily, weekly or monthly.
Status of each terminal managed by this product or the entire security/scan function can be displayed.
Security/Scan Function
Statistical Information
Description
Firewall (FW)
Number of blocked
packets
Number of packets intercepted by FW function
Antivirus (AV)
Number of scanned files Number of files scanned by AV function
Number of blocked files Number of files in which content was rewritten
by AV function
Intrusion Prevention System (IPS)
Number of scanned
flows
Number of traffic flow scanned by IPS function
Number of blocked
flows
Number of traffic flow intercepted by IPS
function
Web Guard (WG)
Number of scanned
URLs
Number of URL scanned by WG function
Number of blocked URLs Number of URL intercepted by WG function
URL Filter (UF)
Number of scanned
URLs
Number of URL scanned by UF function
Number of blocked URLs Number of URL intercepted by UF function
Number of access per
category
Number of access per category of URLs
scanned by monthly UF function
URL Keyword Filter (KF)
Number of scanned
URLs
Number of URL scanned by KF function
Number of blocked URLs Number of URL intercepted by KF function
Application Guard (APG)
Number of scanned
flows
Number of application traffic flow scanned by
APG function
Number of blocked
flows
Number of application traffic flow intercepted
by APG function
Number of applications
accessed
Number of traffic flow of applications scanned
by APG function on a monthly basis
[Saving statistical information]
Regularly saved in memory.
About 7 years
’
worth of statistical information can be saved. After that, older statistical information will be
deleted, and new statistical information is saved.
















































