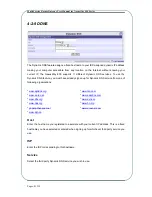
Multi Service Border Gateway User Manual for NexusWay 800 Series
VPN Policy
the public Internet between two remote hosts. VPNs allow the establishment of an encrypted
"tunnel" that protects the network traffic flow from eavesdroppers.
It enables users to access private network data and resources securely over the Internet or
other networks. Even if using public networks, a VPN will inherit the characteristics of a private
network. That’s why it is called "
Virtual
" Private Network. It's used for tunneling, encryption,
authentication, and access control over a public network that supports VPN.
A Virtual Private Network (VPN) is used to provide secure, encrypted communication across
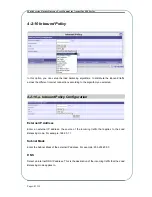
4-3-2-a VPN Policy Configuration
Type
There are two types available, which are Manual Policy and Auto Policy. The most common
configuration, Auto Policy, automatically manages the authentication and encryption keys with
an IKE policy. IKE protocols perform negotiations between two VPN Endpoints to automatically
generate the required parameters. For this reason, you will be required to select a configured
IKE Policy if you select Auto Policy. See
4-3-1 IKE Policy
in this documentation for more
information about IKE Policy configuration. On the other hand, IKE Policies will not be used
with a Manual Policy. All the required key information will be entered manually.
Pages: 93/119