Refer
e
nc
e
Man
ual
for
the
Pr
oSafe
8
02.11
g
Wire
less
VPN F
irewa
ll FVG31
8
Ad
va
nced
Vir
tu
a
l Private Networ
kin
g
7-
13
BETA
Using Digit
al Certificates for
IKE Auto-Policy Authentication
Digita
l c
ertificates
a
re strings ge
ne
rated
using
encryption and authenticatio
n
sc
he
me
s that ca
nnot
be
duplica
ted by a
nyone without acc
ess to the dif
fe
rent values used in the
production of the string.
They are issued by Certification Authorities (CAs
) to
authenti
cate a person or
a
workstation
uniquely
. The CAs a
re
authoriz
ed to is
sue
thes
e
certificates by P
olicy
Certifi
cation Aut
hori
ties
(PCAs), who are in
turn certifi
ed by the
Inte
rnet Policy Regi
stration Authority
(IPRA). The
FVG318 is able
to use certifi
cates
to
authenticate
users
a
t th
e en
d p
oin
ts du
ring
th
e IKE ke
y
exchange proce
ss.
The certificates can be
obtained from
a
certifi
cate se
rver that an
or
ganization might
mainta
in
internally or
from the
est
ablis
hed public CAs. The certificates
are p
rod
uc
ed
b
y p
rov
idin
g th
e
parti
culars
of the user being
identifi
ed to the CA
. The informat
ion
provided may include the user's
na
me, e-m
ail ID,
an
d do
main
na
me.
Enab
le Authentica
tio
n
U
se
thi
s che
ck bo
x to ena
ble or disa
ble ESP
a
uthen
tica
tio
n fo
r
this VPN
p
olicy
.
Authen
tica
tio
n
Algori
th
m
If yo
u e
nab
le
authe
nti
cati
on, th
en use this me
nu to se
lect
the
a
lgori
thm:
•
M
D5
— th
e defaul
t
•
S
HA1
— more secure
Key -
In
Enter
the key
.
•
F
or MD5,
the key shou
ld be 16
cha
racte
rs.
•
F
or SHA-1,
the key shou
ld be 20 cha
ra
cte
rs.
An
y
va
lue
is accept
abl
e, provid
ed t
he re
mo
te
VPN
end
p
oint ha
s th
e same
va
lue in
it
s Au
th
enticatio
n
Al
gorithm Key
- Out fiel
d.
Key - Out
E
n
te
r the key in th
e fi
elds provi
ded.
•
F
or MD5,
the key shou
ld be 16
cha
racte
rs.
•
F
or SHA-1,
the key shou
ld be 20 cha
ra
cte
rs.
An
y
va
lue
is accept
abl
e, provid
ed t
he re
mo
te
VPN
end
p
oint ha
s th
e same
va
lue in
it
s Au
th
enticatio
n
Al
gorithm Key
- In fie
ld.
NETBIOS Enable
C
heck thi
s
if you wish
NET
B
IOS
traf
fic to
be
forwa
rded ove
r the VPN
tun
nel.
Th
e N
E
TBIOS
protocol
is
used
b
y Microso
ft Ne
tw
orking
for
su
ch
fe
at
ur
es
as
N
e
tw
or
k N
eig
hb
or
ho
o
d.
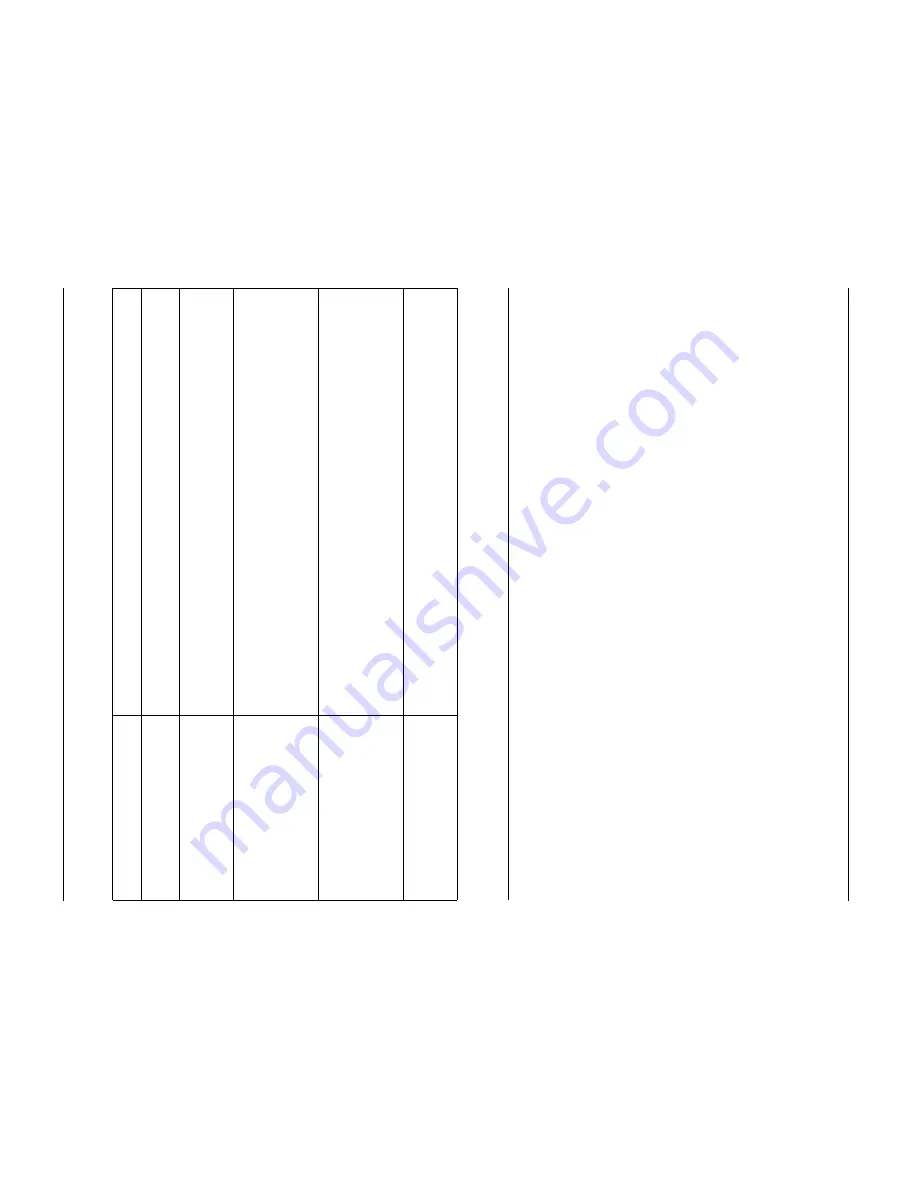
Ta
ble 7-
1.
VPN
M
a
nua
l Poli
cy Conf
igura
tion Fields
Field D
escr
ip
tio
n












































