Version 2.0
Creating your own Certificate Authority with OpenSSL
1- In first step you need to create your own CA. To do that, follow the instructions
documented in here:
http://sandbox.rulemaker.net/ngps/m2/howto.ca.html
2- Netgear doesn’t support ST relative distinguish name so please edit the openssl.cfg (in
the original location and in your new CA folder) to avoid using this parameter.
3-
From the guide linked above, you need only to execute all the commands up to step 4.
The certificate request step and beyond will be handled by the router.
4-
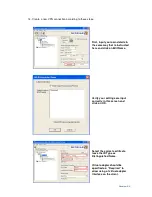
Next – please generate Self Certificate Request specifying the following parameters:
1- Name: first
2- Subject: CN=router1
3- Hash Algorithm: MD5
4- Signature Algorithm: RSA
5- Signature Key Length: 1024
6- Click on Generate
5- Click on: “
View
” for generated certificate request to check its values:
Copy all the information from
the
Data to supply to CA
field
to the text file
router1.csr