ProSecure Web/Email Security Threat Management (STM) Appliance Reference Manual
5-8
Managing Users, Groups, and Authentication
v1.0, September 2009
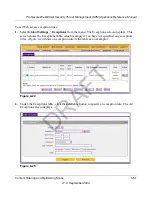
The List of Users table displays the users with the following fields:
•
Enable
.
The checkbox allows you to enable or disable the user.
•
Name
. The name of the user.
•
Group
. The group to which the user is assigned. If no group is displayed, the user is not
assigned to any group.
•
Action
. The edit table button that provides access to the Edit User screen and the delete
table button that allows you to delete the user.
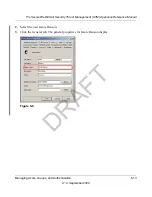
2.
In the Add New Users section of the screen, complete the fields, make your selection from the
pull-down menu, and select the radio buttons as explained in
Table 5-4 on page 5-8
.
3.
Click the
add
table button. The new user is added to the List of Users table.
To delete a user from the List of Users table, click the
delete
table button in the Action column for
the user that you want to delete.
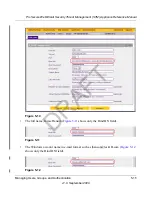
Editing User Accounts
The only field that you can change for a user account is the password. To modify the password for
a user:
1.
Select
Users
>
Users
from the menu. The Users screen displays (see
Figure 5-4 on page 5-7
).
Table 5-4. User Settings
Setting
Description
Name
A descriptive (alphanumeric) name of the user for identification and
management purposes.
Groups
The pull-down menu shows the local groups that are listed on the Group
screen. From the pull-down menu, select the group to which the user will be
assigned. For information about how to configure groups, see
“Configuring
Groups” on page 5-2
.
Password
Select one of the following radio buttons:
•
The radio button to the left of the Password field
. Enter the password that
the user must enter to gain access to the STM. The password can be up to
64 characters.
•
Use username as the password
. The password that is assigned to the user
is identical to the user name.
DRAFT