ProSecure Web/Email Security Threat Management (STM) Appliance Reference Manual
6-28
Monitoring System Access and Performance
v1.0, September 2009
To identify infected clients that are sending spyware or a virus in outbound traffic, query the STM
spyware and virus logs and see if any of your internal IP addresses are the source of spyware or a
virus:
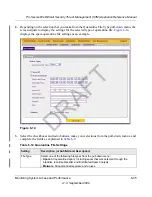
1.
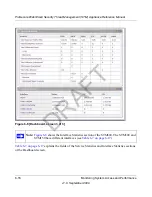
On the Log Query screen (see
Figure 6-11 on page 6-24
), select
Traffic
as the log type.
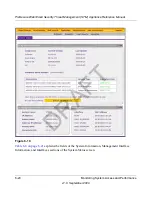
2.
Select the start date and time from the pull-down menus.
3.
Select the end date and time from the pull-down menus.
4.
Next to Protocols, select the
HTTP
checkbox.
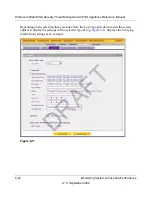
5.
Click
Search
. After a while, the log appears on screen.
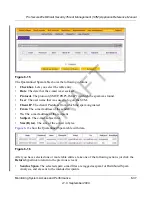
6.
Check if there are clients that are sending out suspicious volumes of data, especially to the
same destination IP address, on a regular basis.
If you find a client exhibiting this behavior, you can run a query on that client’s HTTP traffic
activities to get more information. Do so by running the same HTTP traffic query and entering the
client IP address in the Client IP field.
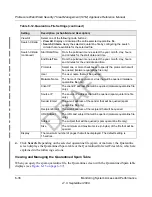
Log Management
Generated logs take up space and resources on the STM internal disk. To ensure that there is
always sufficient space to save newer logs, the STM automatically deletes older logs whenever the
total log size reaches 50% of the allocated file size for each log type.
Automated log purging means that you do not need to constantly manage the size of the STM logs
and ensures that the latest malware incidents and traffic activities are always recorded.
To manually purge selected logs, see
“Clearing Logs” on page 6-7
.
Note:
After the STM has restarted, traffic logs are lost. Therefore, NETGEAR
recommends that you connect the STM to a syslog server to save the traffic logs
externally. Other logs (that is, non-traffic logs) are automatically backed up on the
STM every 15 minutes. However, if a power failure affects the STM, logs that
where created within this 15-minute period are lost.
DRAFT