ProSecure Web/Email Security Threat Management (STM) Appliance Reference Manual
6-34
Monitoring System Access and Performance
v1.0, September 2009
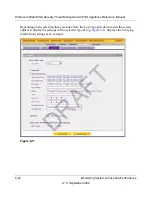
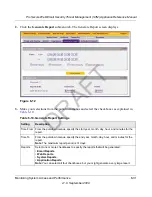
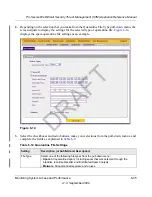
You can query and view the spam quarantine file and the malware quarantine file separately and
filter the information based on a number of criteria. You can filter the spam quarantine file using
the following criteria:
•
Start date and time
•
End date and time
•
User name
•
Source IP address
•
Sender e-mail address
•
Recipient e-mail address
•
Subject
•
Size of the e-mail
You can filter the malware quarantine file using the following criteria:
•
Start date and time
•
End date and time
•
Protocols (SMTP, POP3, IMAP, HTTP, FTP, HTTPS)
•
User name
•
Malware name
•
Client IP address
•
Recipient e-mail address
•
Recipient e-mail address
•
URL or subject
•
Size of the file
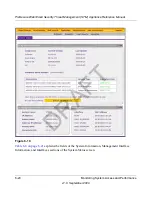
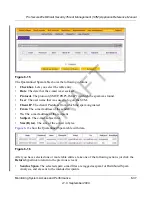
To query the quarantine files:
1.
Select
Monitoring
>
Quarantine
from the menu. The Quarantine screen displays (see
Figure 6-14 on page 6-35
).
Note:
To specify the quarantine settings, see
“Managing the Quarantine Settings” on
page 3-31
.
DRAFT