ProSecure Web/Email Security Threat Management (STM) Appliance Reference Manual
Performing Network and System Management
3-25
v1.0, September 2009
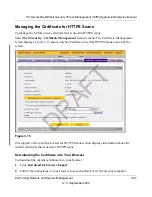
Managing Digital Certificates
The STM uses digital certificates (also known as X509 certificates) for secure web access
connections over HTTPS (that is, SSL VPN connections).
Digital certificates can be either self-signed or can be issued by certification authorities (CAs) such
as an internal Windows server or an external organizations such as Verisign or Thawte. On the
STM, the uploaded digital certificate is checked for validity and purpose. The digital certificate is
accepted when it passes the validity test and the purpose matches its use.
The STM uses digital certificates to authenticate connecting HTTPS servers, and to allow HTTPS
clients to be authenticated by remote entities. A digital certificate that authenticates a server, for
example, is a file that contains the following elements:
•
A public encryption key to be used by clients for encrypting messages to the server.
•
Information identifying the operator of the server.
•
A digital signature confirming the identity of the operator of the server. Ideally, the signature is
from a trusted third party whose identity can be verified.
Note:
If you select the default NTP servers or if you enter a custom server FQDN, the
STM will determine the IP address of the NTP server by performing a DNS
lookup. You must configure a DNS server address in the Network menu before the
STM can perform this lookup.
DRAFT