ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
Content Filtering and Optimizing Scans
6-21
v1.0, September 2009
3.
Click
Apply
to save your settings
Configuring Web Malware Scans
Whether or not the UTM detects Web-based malware threats, you can configure it to take a variety
of actions (some of the default actions are listed in
Table 6-1 on page 6-2
) and send notifications,
e-mails, or both to the end users.
To configure the Web-based malware settings:
1.
Select
Application
Security
>
HTTP/HTTPS
from the menu. The HTTP/HTTPS submenu
tabs appear, with the Malware Scan screen in view (see
Figure 6-8 on page 6-22
).
Note
: If a protocol uses a port other than the standard service port (for example, port 80 for HTTP),
enter this non-standard port in the Ports to Scan field. For example, if the HTTP service on your
network uses both port 80 and port 8080, enter both port numbers in the Ports to Scan field and
separate them by a comma.
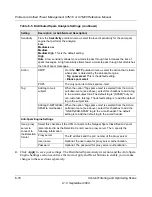
Instant Messaging
Google Talk (Jabber)
Select the corresponding checkboxes to block any of these common instant
messaging services, all of which are allowed by default.
Note:
For Instant Messaging services, the following services can be blocked:
logging in, sharing files, sharing video, sharing audio, and text messaging.
Yahoo messenger
mIRC
Skype
MSN Messenger
Peer-to-Peer (P2P)
BitTorrent
Select the corresponding checkboxes to block any of these common peer-to-
peer file sharing services, all of which are allowed by default.
eDonkey
Gnutella
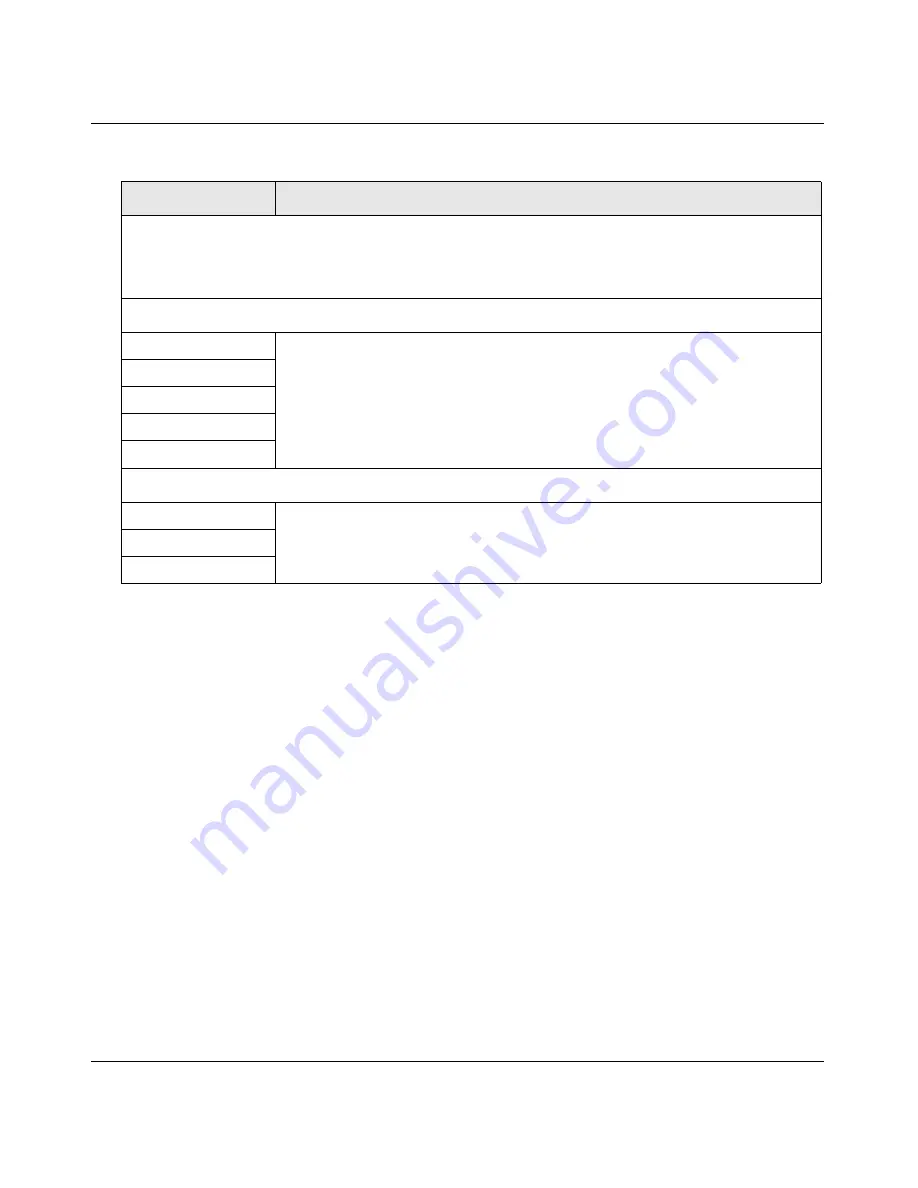
Table 6-6. Web Protocol, Instant Messaging, and Peer-to-Peer Settings (continued)
Setting
Description (or Subfield and Description)