ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
Virtual Private Networking Using IPsec Connections
7-31
v1.0, September 2009
2.
Click the
VPN Policies
submenu tab.
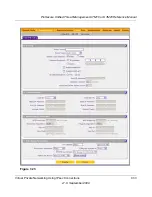
The VPN Policies screen display. (
Figure 7-22
shows
some examples.)
Each policy contains the data that are explained in
Table 7-11
. These fields are explained in
more detail in
Table 7-12 on page 7-34
.
Figure 7-22
Table 7-11. List of VPN Policies Information
Item
Description (or Subfield and Description)
! (Status)
Indicates whether the policy is enabled (green circle) or disabled (grey circle). To
enable or disable a policy, select the checkbox adjacent to the circle and click
the
enable
or
disable
table button, as required.
Name
The name that identifies the VPN policy. When you use the VPN Wizard to
create a VPN policy, the name of the VPN policy (and of the automatically
created accompanying IKE policy) is the Connection Name.
Type
“Auto” or “Manual” as described previously (Auto is used during VPN Wizard
configuration).
Local
IP address (either a single address, range of address or subnet address) on your
local LAN. Traffic must be from (or to) these addresses to be covered by this
policy. (The subnet address is supplied as the default IP address when using the
VPN Wizard).
Remote
IP address or address range of the remote network. Traffic must be to (or from)
these addresses to be covered by this policy. (The VPN Wizard default requires
the remote LAN IP address and subnet mask).
Auth
The authentication algorithm that is used for the VPN tunnel. This setting must
match the setting on the remote endpoint.