ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
Monitoring System Access and Performance
11-13
v1.0, September 2009
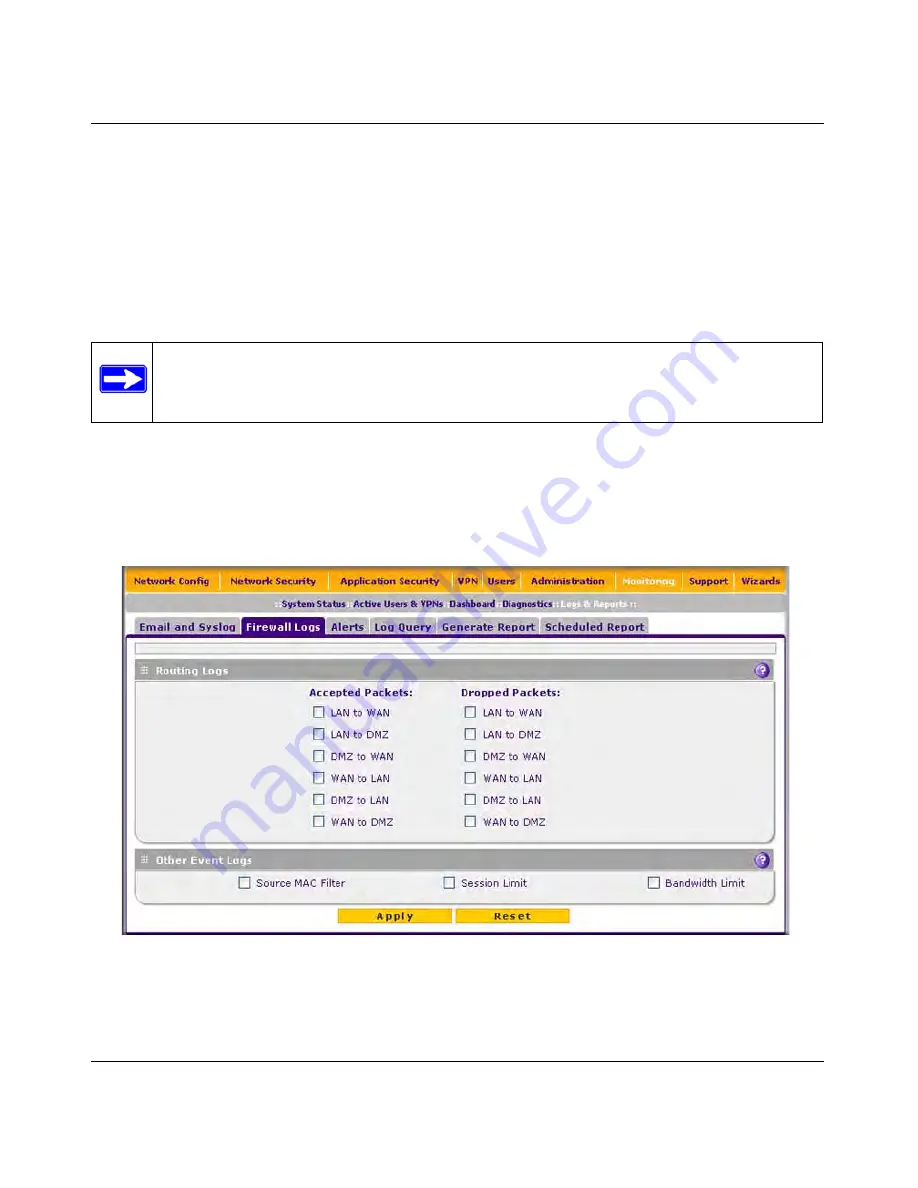
Configuring and Activating Firewall Logs
You can configure the logging options for each network segment. For example, the UTM can log
accepted packets for LAN-to-WAN traffic, dropped packets for WAN-to-DMZ traffic, and so on.
You can also configure logging of packets from MAC addresses that match the source MAC
address filter settings (see
“Enabling Source MAC Filtering” on page 5-40
), and packets that are
dropped because the session limit (see
“Setting Session Limits” on page 5-23
), bandwidth limit
(see
“Creating Bandwidth Profiles” on page 5-36
), or both, have been exceeded.
To configure and activate firewall logs:
1.
Select
Monitoring
>
Logs & Reports
from the menu. The Logs & Reports submenu tabs
appear, with the Email and Syslog screen in view.
2.
Click the
Firewall Logs
submenu tab.
The Firewall Logs screen displays (see
Figure 11-6
).
3.
Enter the settings as explained in
Table 11-5 on page 11-14
.
Note:
Enabling firewall logs might generate a significant volume of log messages.
NETGEAR recommends that you enable firewall logs for debugging purposes
only.
Figure 11-6