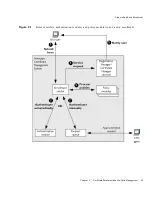
System Architecture
Chapter
1
Introduction to Certificate Management System
75
One or more PKCS #11 modules must be available to any CMS subsystem instance.
As shown in Figure 1-10, a PKCS #11 module (also called a cryptographic module or
cryptographic service provider) manages cryptographic services such as encryption
and decryption via the PKCS #11 interface. PKCS #11 modules can be thought of as
drivers for cryptographic devices that can be implemented in either hardware or
software. Netscape provides a built-in PKCS #11 module with Certificate
Management System; see “Installing External Tokens” on page 432.
A PKCS #11 module always has one or more slots, which can be implemented as
physical hardware slots in some form of physical reader (for example, for smart
cards) or as conceptual slots in software. Each slot for a PKCS #11 module can in
turn contain a token, which is the hardware or software device that actually
provides cryptographic services and optionally stores certificates and keys.
Netscape provides two built-in modules with Certificate Management System:
•
Default Netscape Internal PKCS #11 Module.
This comes with two built-in
tokens:
❍
The Internal Crypto Services token performs all cryptographic operations,
such as encryption, decryption, and hashing.
❍
The Internal Key Storage token (“Certificate DB token” in Figure 1-10)
handles all communication with the certificate and key database files
(called
certX.db
and
keyX.db
, respectively, where
X
is a version number)
that store certificates and keys.
•
FIPS 140-1 module.
This module complies with the FIPS 140-1 government
standard for implementations of cryptographic modules. Many products sold
to the US government must comply with one or more of the FIPS standards.
The FIPS 140-1 module includes a single, built-in FIPS 140-1 Certificate DB
token (see Figure 1-10), which handles both cryptographic operations and
communication with the
certX.db
and
keyX.db
files.
Any PKCS #11 module can be used with Certificate Management System. The
server uses a file called
secmod.db
to keep track of the modules that are available.
You can modify this file with the Security Module Database Tool explained in the
CMS Command-Line Tools Guide. For example, you need to modify
secmod.db
if
you are installing hardware accelerators for use in signing operations.
Summary of Contents for NETSCAPE MANAGEMENT SYSTEM 6.0
Page 1: ...Installation and Setup Guide Netscape Certificate Management System Version6 0 March 2002...
Page 22: ...22 Netscape Certificate Management System Installation and Setup Guide March 2002...
Page 32: ...32 Netscape Certificate Management System Installation and Setup Guide March 2002...
Page 160: ...160 Netscape Certificate Management System Installation and Setup Guide March 2002...
Page 776: ...776 Netscape Certificate Management System Installation and Setup Guide March 2002...
Page 807: ...807 Part 5 Appendix Appendix A Certificate Download Specification...
Page 808: ...808 Netscape Certificate Management System Installation and Setup Guide March 2002...
Page 830: ...830 Netscape Certificate Management System Installation and Setup Guide March 2002...