Nortel Switched Firewall 2.3.3 User’s Guide and Command Reference
Redundant Firewalls
185
213455-L, October 2005
Establishing trust on redundant Firewalls
The ability to establish trust—Secure Internal Communication (SIC)—on redundant firewalls
is required so that you can push policies to them from the Check Point SmartCenter Server.
N
OTE
–
Static routes must be added if your management station is on a different network from
the Firewall host network.
In the following example the management station is behind the Firewall—a common
strategy— on the same network as the virtual router interface (see
Figure 58 on page 126
).
Establishing trust from a management sation behind the
Firewall
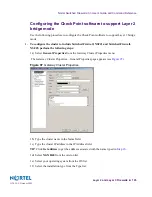
To establish trust from a management station behind the Firewall, perform the following steps:
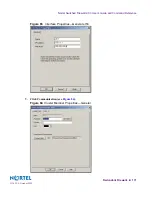
1.
Open a DOS window on the management station and enter a static route between addr1
and the host #1 IP address.
For this example, the management station interface IP address is 10.10.1.200. Use the addr1 IP
address as the gateway.
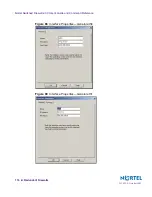
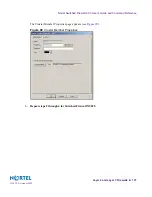
2.
Enter a static route between addr2 and the host #2 IP address.
TIP
: Use the addr2 IP address as the gateway.
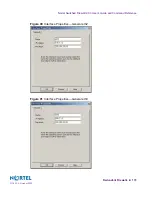
3.
At the local console, add the management station IP address to the cluster access list.
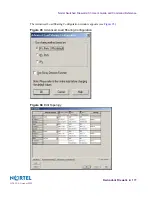
4.
From the Check Point SmartDashboard, establish trust with both Firewall objects
(firewall host #1 and firewall host #2). See
Re-establishing SIC on page 410
.
C:\ route add 10.10.1.193 mask 255.255.255.255 33.1.1.12 -p
^destination ^mask ^gateway
C:\ route add 10.10.1.194 mask 255.255.255.255 33.1.1.13 -p
>> Main# /cfg/sys/accesslist/add
Enter network address: 10.10.1.200
Management station IP address
Enter netmask: 255.255.255.0
>> Main# apply
Applies data to both firewalls