Nortel Switched Firewall 2.3.3 User’s Guide and Command Reference
Layer 2 and Layer 3 Firewalls
211
213455-L, October 2005
8.
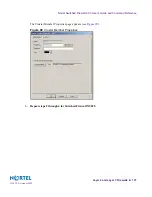
To configure topology for the cluster, perform the following steps:
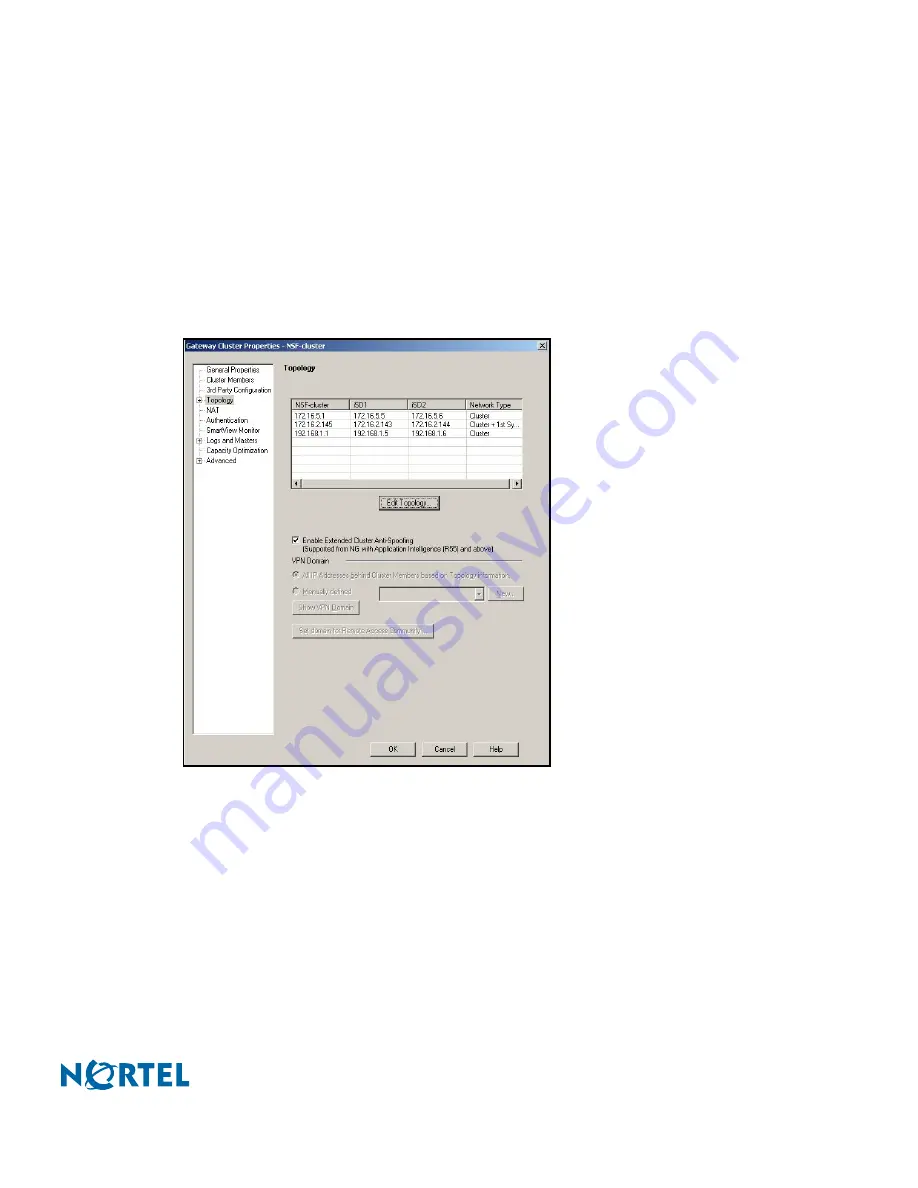
8a) From the Gateway Cluster Properties menu, select
Topology
.
The Gateway Cluster Properties—Topology page appears (see
Figure 110
).
8b) Select
Enable Extended Cluster Anti-Spoofing
.
The Check Point software disables Address Spoofing on bridge ports unless they are manually
added to the configuration (eth2 and eth3 are bridge ports).
Figure 110
Gateway Cluster Properties—Topology
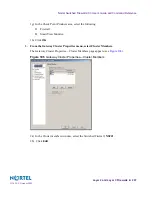
9.
Click Edit Topology.
The Edit Topology page appears (see
Figure 111
).