Nortel Switched Firewall 2.3.3 User’s Guide and Command Reference
30
Initial setup
213455-L, October 2005
Basic requirements
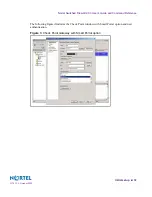
The following are needed before you configure the Nortel Switched Firewall:
Firewall hardware must be installed as described in the
Nortel Switched Firewall 5100
Series Hardware Installation Guide
(216382-D)
.
Installation includes mounting the
components, attaching network cables, turning on power, and connecting a console
terminal.
A Check Point license must exist for the Firewall.
One subnet must be assigned for internal Nortel Switched Firewall use. This subnet must
consist of the following IP addresses:
one Management IP (MIP) address
an IP address for the Firewall host
N
OTE
–
The highest IP address and lowest IP address in the subnet range are reserved for
broadcasts and should not be assigned to specific devices.
A list of subnets that will be statically configured on the firewall for internal networks,
plus the IP address of the internal router that handles routes for these networks.
The IP address of the default gateway for data moving through the firewall to the Internet.
An IP address reserved for the Firewall on each trusted, untrusted, and semi-trusted subnet
that will connect directly to the Firewall.
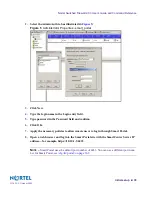
A SmartCenter Server and SMART Client on one of the networks attached to the Firewall.
You can install the SmartCenter Server on the Switched Firewall or on a remote
management station (Note – If you have two Switched Firewalls in the cluster, you must
implement the SmartCenter Server on the management station). You can install the
SMART Client on the same machine as the SmartCenter Server, or on a separate machine
that can be reached from the SmartCenter Server.
N
OTE
–
This release of the Switched Firewall supports Check Point VPN-1 and FireWall-1
NGX with Application Intelligence (R60) and Hotfix Accumulator 14 (HFA_14) software.
Nortel Switched Firewall installed running Firewall OS version 2.3.3 or higher.