Nortel Switched Firewall 2.3.3 User’s Guide and Command Reference
Initial setup
85
213455-L, October 2005
Layer 2 switch configuration
To ensure that each of the DMZ areas is privately and securely connected to the Switched
Firewall, the following configuration steps must be taken on the layer 2 switches:
Configure DMZ access ports on the layer 2 switch as members of the corresponding
VLAN. In this example, DMZ A is VLAN ID 10; DMZ B is VLAN ID 11. The switch
must add a VLAN tag to untagged frames entering the port.
Configure the trunk (uplink) port as a member of each DMZ VLAN and as a tagged trunk
port.
Disable any unused ports and filter any tagged traffic on ports that are not VLAN
members.
Ensure that auto-learning is disabled on the trunk port and the MAC address of the
Switched Firewall is configured on the switch.
If VLANs are configured on the interface, then TAG is always enabled. However, Windows
PCs must be tagged if they are connected directly to the interface. Or, you can add a 802.1q-
capable Layer 2 switch between the PC and the firewall.
SmartDashboard configuration
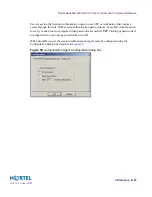
Prior to performing these steps, ensure that the Check Point SmartCenter Server is configured
and trust is established between the SmartCenter Server and the firewall host.
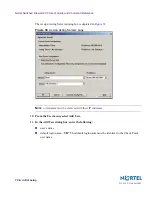
You must configure the topology and define interface properties for the firewall. Ensure that
the interface (47.133.63.99) facing the Internet is defined as “external.” Make sure that the
other networks are defined as “internal”, with addresses behind the gateway defined by the
interface IP and netmask. Also, name the networks for use in the SmartDashboard as follows:
10.10.1.0: “NSF-Private”
33.1.1.0: “Intranet”
47.133.63.0 “Internet”
192.168.0.0: “DMZ-1”
192.168.2.0: “DMZ-2”
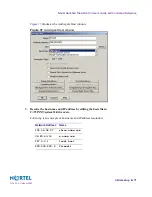
To create a network object for the public web server in DMZ-1, perform the following steps:
1.
Right-click the Network Topology window.
The shortcut menu appears.
2.
Select New Network Object > Workstation from the shortcut menu.