238
Chapter 13 VPN
NN47923-500
IKE phases
There are two phases to every IKE (Internet Key Exchange) negotiation–phase 1
(Authentication) and phase 2 (Key Exchange). A phase 1 exchange establishes an
IKE SA and the second one uses that SA to negotiate SAs for IPSec.
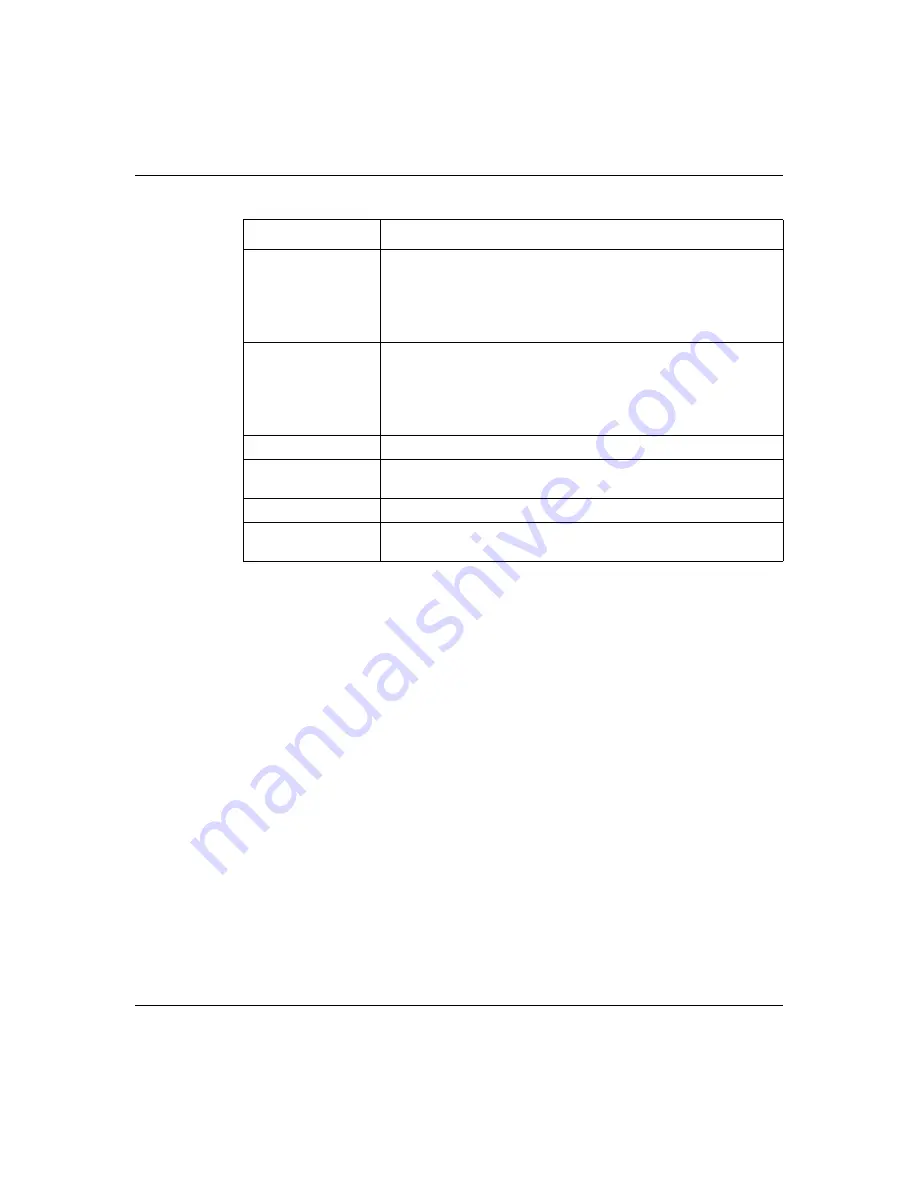
Start Port
Type a port number in this field.
To forward only one port, type the port number again in the
End
Port
field.
To forward a series of ports, type the start port number here and
the end port number in the
End Port
field.
End Port
Type a port number in this field.
To forward only one port, type the port number in the
Start Port
field above and then type it again in this field.
To forward a series of ports, type the last port number in a series
that begins with the port number in the
Start Port
field above.
Server IP Address
Type your server IP address in this field.
Apply
Click this button to save these settings and return to the
VPN
Branch Office - IP Policy
screen.
Reset
Click this button to begin configuring this screen afresh.
Cancel
Click this button to return to the
VPN Branch Office - IP Policy
screen without saving your changes.
Table 56
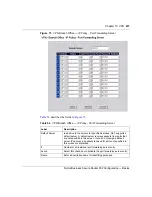
VPN Branch Office — IP Policy - Port Forwarding Server
Label
Description
Summary of Contents for BSR252
Page 28: ...28 Tables NN47923 500 ...
Page 44: ...44 Chapter 1 Getting to know your Business Secure Router NN47923 500 ...
Page 52: ...52 Chapter 2 Introducing the WebGUI NN47923 500 ...
Page 70: ...70 Chapter 3 Wizard setup NN47923 500 ...
Page 96: ...96 Chapter 5 System screens NN47923 500 ...
Page 114: ...114 Chapter 7 WAN screens NN47923 500 Figure 27 WAN IP ...
Page 120: ...120 Chapter 7 WAN screens NN47923 500 Figure 31 Dial Backup Setup ...
Page 128: ...128 Chapter 7 WAN screens NN47923 500 ...
Page 152: ...152 Chapter 9 Static Route screens NN47923 500 ...
Page 194: ...194 Chapter 11 Firewall screens NN47923 500 ...
Page 210: ...210 Chapter 13 VPN NN47923 500 Figure 67 Summary IP Policies ...
Page 222: ...222 Chapter 13 VPN NN47923 500 Figure 71 VPN Branch Office rule setup ...
Page 256: ...256 Chapter 13 VPN NN47923 500 Figure 81 VPN Client Termination advanced ...
Page 260: ...260 Chapter 13 VPN NN47923 500 ...
Page 264: ...264 Chapter 14 Certificates NN47923 500 Figure 83 My Certificates ...
Page 270: ...270 Chapter 14 Certificates NN47923 500 Figure 85 My Certificate create ...
Page 274: ...274 Chapter 14 Certificates NN47923 500 Figure 86 My Certificate details ...
Page 282: ...282 Chapter 14 Certificates NN47923 500 Figure 89 Trusted CA details ...
Page 298: ...298 Chapter 14 Certificates NN47923 500 ...
Page 316: ...316 Chapter 16 IEEE 802 1x NN47923 500 ...
Page 320: ...320 Chapter 17 Authentication server NN47923 500 Figure 106 Local User database edit ...
Page 328: ...328 Chapter 17 Authentication server NN47923 500 ...
Page 376: ...376 Chapter 20 Logs Screens NN47923 500 Figure 150 Log settings ...
Page 386: ...386 Chapter 20 Logs Screens NN47923 500 ...
Page 393: ...Chapter 21 Call scheduling screens 393 Nortel Business Secure Router 252 Configuration Basics ...
Page 394: ...394 Chapter 21 Call scheduling screens NN47923 500 ...
Page 410: ...410 Chapter 22 Maintenance NN47923 500 ...