Chapter 3 Wizard setup
55
Nortel Business Secure Router 252 Configuration — Basics
VC-based multiplexing
In this case, by prior mutual agreement, each protocol is assigned to a specific
virtual circuit; for example, VC1 carries IP. VC-based multiplexing can be
dominant in environments where dynamic creation of large numbers of ATM VCs
is fast and economical.
LLC-based multiplexing
In this case, one VC carries multiple protocols with protocol-identifying
information being contained in each packet header. Despite the extra bandwidth
and processing overhead, this method can be advantageous if it is not practical to
have a separate VC for each carried protocol, for example, if charging heavily
depends on the number of simultaneous VCs.
VPI and VCI
Be sure to use the correct Virtual Path Identifier (VPI) and Virtual Channel
Identifier (VCI) numbers assigned to you. The valid range for the VPI is 0 to 255
and 32 to 65535 for the VCI (0 to 31 is reserved for local management of ATM
traffic).
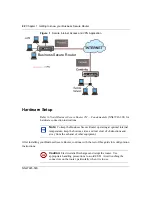
Wizard setup configuration: first screen
In the
Site Map
screen, click
Wizard Setup
to display the first wizard screen.
Summary of Contents for BSR252
Page 28: ...28 Tables NN47923 500 ...
Page 44: ...44 Chapter 1 Getting to know your Business Secure Router NN47923 500 ...
Page 52: ...52 Chapter 2 Introducing the WebGUI NN47923 500 ...
Page 70: ...70 Chapter 3 Wizard setup NN47923 500 ...
Page 96: ...96 Chapter 5 System screens NN47923 500 ...
Page 114: ...114 Chapter 7 WAN screens NN47923 500 Figure 27 WAN IP ...
Page 120: ...120 Chapter 7 WAN screens NN47923 500 Figure 31 Dial Backup Setup ...
Page 128: ...128 Chapter 7 WAN screens NN47923 500 ...
Page 152: ...152 Chapter 9 Static Route screens NN47923 500 ...
Page 194: ...194 Chapter 11 Firewall screens NN47923 500 ...
Page 210: ...210 Chapter 13 VPN NN47923 500 Figure 67 Summary IP Policies ...
Page 222: ...222 Chapter 13 VPN NN47923 500 Figure 71 VPN Branch Office rule setup ...
Page 256: ...256 Chapter 13 VPN NN47923 500 Figure 81 VPN Client Termination advanced ...
Page 260: ...260 Chapter 13 VPN NN47923 500 ...
Page 264: ...264 Chapter 14 Certificates NN47923 500 Figure 83 My Certificates ...
Page 270: ...270 Chapter 14 Certificates NN47923 500 Figure 85 My Certificate create ...
Page 274: ...274 Chapter 14 Certificates NN47923 500 Figure 86 My Certificate details ...
Page 282: ...282 Chapter 14 Certificates NN47923 500 Figure 89 Trusted CA details ...
Page 298: ...298 Chapter 14 Certificates NN47923 500 ...
Page 316: ...316 Chapter 16 IEEE 802 1x NN47923 500 ...
Page 320: ...320 Chapter 17 Authentication server NN47923 500 Figure 106 Local User database edit ...
Page 328: ...328 Chapter 17 Authentication server NN47923 500 ...
Page 376: ...376 Chapter 20 Logs Screens NN47923 500 Figure 150 Log settings ...
Page 386: ...386 Chapter 20 Logs Screens NN47923 500 ...
Page 393: ...Chapter 21 Call scheduling screens 393 Nortel Business Secure Router 252 Configuration Basics ...
Page 394: ...394 Chapter 21 Call scheduling screens NN47923 500 ...
Page 410: ...410 Chapter 22 Maintenance NN47923 500 ...