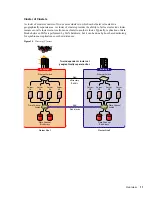
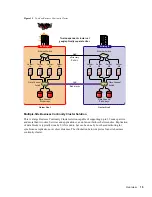
Summary of Contents for BUSINESS CONTINUITY CLUSTERING 1.1 SP1
Page 6: ...6 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...
Page 8: ...8 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...
Page 58: ...58 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...
Page 84: ...84 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...
Page 96: ...96 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...