Installation and Setup
57
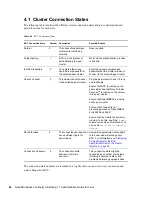
Primary Cluster and Primary SAN Both Fail
Bring up your primary SAN or iSCSI target before bringing up your cluster servers. Then run the
Cluster Scan For New Devices
command from a secondary cluster server. Ensure that
remirroring completes before bringing downed cluster servers back up.
If necessary, promote the former primary SAN back to primary. Then bring up the former primary
cluster servers and fail back the cluster resources.
Secondary Cluster Fails but Secondary SAN Does Not
No additional response is necessary for this failure other than recovering the secondary cluster.
When you bring the secondary cluster back up, the LUNs will still be in a secondary state to the
primary SAN.
Secondary Cluster and Secondary SAN Both Fail
Bring up your secondary SAN or iSCSI target before bringing up your cluster servers. Then run the
Cluster Scan For New Devices
command on a primary cluster server to ensure remirroring
takes place. When you bring the secondary cluster back up, the LUNs are still in a secondary state to
the primary SAN.
Primary SAN Fails but Primary Cluster Does Not
If your primary SAN fails, all nodes in your primary cluster also fail. Bring up your primary SAN or
iSCSI target and then bring up your cluster servers. Then run the
Cluster Scan For New
Devices
command from a secondary cluster server. Ensure that remirroring completes before
bringing downed cluster servers back up.
If necessary, promote the former primary SAN back to primary. You might need to demote the
LUNs and resources to secondary on the primary SAN before bringing them back up. You can use
the
cluster resetresources
console command to change resource states to offline and
secondary. Bring up the former primary cluster servers and fail back the resources.
Secondary SAN Fails but Secondary Cluster Does Not
Bring up your secondary SAN or iSCSI target before bringing up your cluster servers. Then run the
Cluster Scan For New Devices
command on a primary cluster server to ensure that remirroring
takes place. Then bring the secondary cluster back up. When you bring the secondary SAN and
cluster back up, resources are still in a secondary state.
Intersite SAN Connectivity is Lost
You must run the
Cluster Scan For New Devices
command on both clusters to ensure
remirroring takes place. Recover your SANs first, then remirror from the good side to the bad side.
Intersite LAN Connectivity is Lost
Users might not be able to access servers in the primary cluster but can possibly access servers in the
secondary cluster. If both clusters are up, nothing additional is required. An error is displayed. Wait
for connectivity to resume.
If you have configured the auto-failover feature, see
Appendix B, “Setting Up Auto-Failover,” on
page 85
.
Summary of Contents for BUSINESS CONTINUITY CLUSTERING 1.1 SP1
Page 6: ...6 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...
Page 8: ...8 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...
Page 58: ...58 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...
Page 84: ...84 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...
Page 96: ...96 Novell Business Continuity Clustering 1 1 Administration Guide for Linux...