42
Identity Manager 3.6.1 Reporting Guide for Novell Sentinel
no
vd
ocx
(e
n)
17
Sep
te
m
be
r 20
09
2
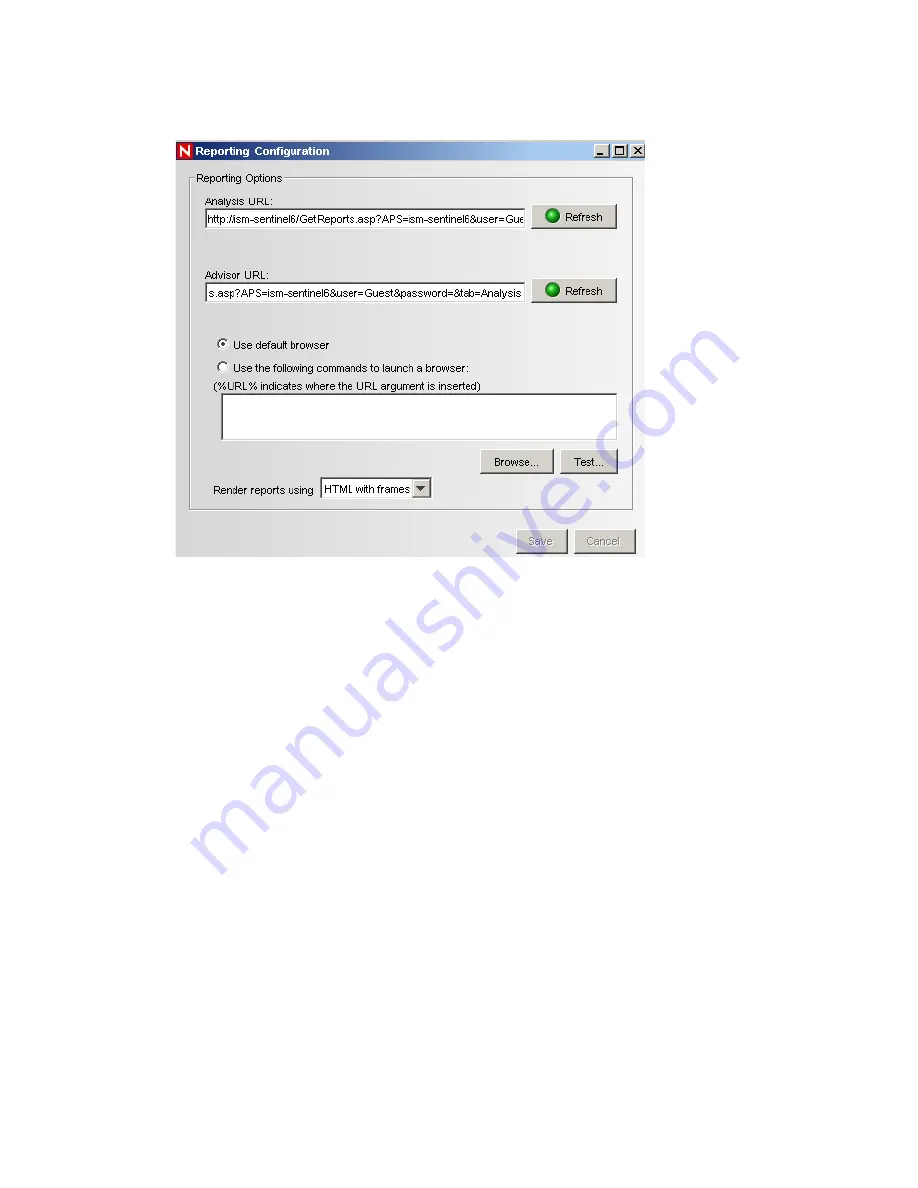
Specify the location of the Crystal Enterprise server, then click
Save
.
After Novell Sentinel is configured to access the Crystal Enterprise server, the Analysis page allows
administrators to run historical reports. Vulnerability reports are available from the Advisor page.
These reports are published on a Web server, they run directly against the database, and they then
appear on the
Analysis
and
Advisor
tabs under the Navigator pane.
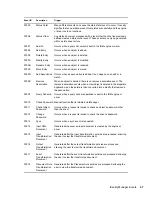
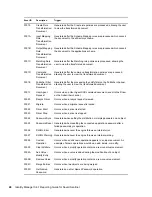
The reports are updated regularly. The following is a list of the categories of reports that are
available:
Collector Pack Controls:
Contains reports about the Collector Pack setup, dashboard status,
and implementation of audit trails.
Collector Controls:
Contains reports about event trends and Collector management.
Account Management Controls:
Contains reports about user account provisioning, user
account management, account access management, and user password management.
Trust Management Controls:
Contains reports about trust provisioning, trust management,
and trust access management.
Object Management Controls:
Contains reports about object provisioning and object
management.
Authentication Controls:
Contains reports about authentication by servers and users.
Workflow Management:
Contains reports that monitor workflows and the resources
requested in the workflows.
For more information on running reports in Novell Sentinel, see the “Analysis Tab” and “Advisor
Usage and Maintenance” sections in the
Novell Sentinel User’s Guide
(http://www.novell.com/
documentation/sentinel61/pdfdoc/sentinel_61_user_guide.pdf)
.
Summary of Contents for IDENTITY MANAGER 3.6.1
Page 4: ...4 Identity Manager 3 6 1 Reporting Guide for Novell Sentinel novdocx en 17 September 2009 ...
Page 12: ...12 Identity Manager 3 6 1 Reporting Guide for Novell Sentinel novdocx en 17 September 2009 ...
Page 16: ...16 Identity Manager 3 6 1 Reporting Guide for Novell Sentinel novdocx en 17 September 2009 ...
Page 20: ...20 Identity Manager 3 6 1 Reporting Guide for Novell Sentinel novdocx en 17 September 2009 ...
Page 24: ...24 Identity Manager 3 6 1 Reporting Guide for Novell Sentinel novdocx en 17 September 2009 ...
Page 26: ...26 Identity Manager 3 6 1 Reporting Guide for Novell Sentinel novdocx en 17 September 2009 ...
Page 54: ...54 Identity Manager 3 6 1 Reporting Guide for Novell Sentinel novdocx en 17 September 2009 ...