52
ZENworks Endpoint Security Management Installation Guide
no
vd
ocx
(e
n)
17
Sep
te
m
be
r 20
09
2
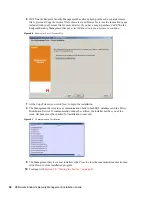
(Optional) To load users and new groups to this list:
2a
Click the
Add
button on the bottom of the screen to display the Organization table.
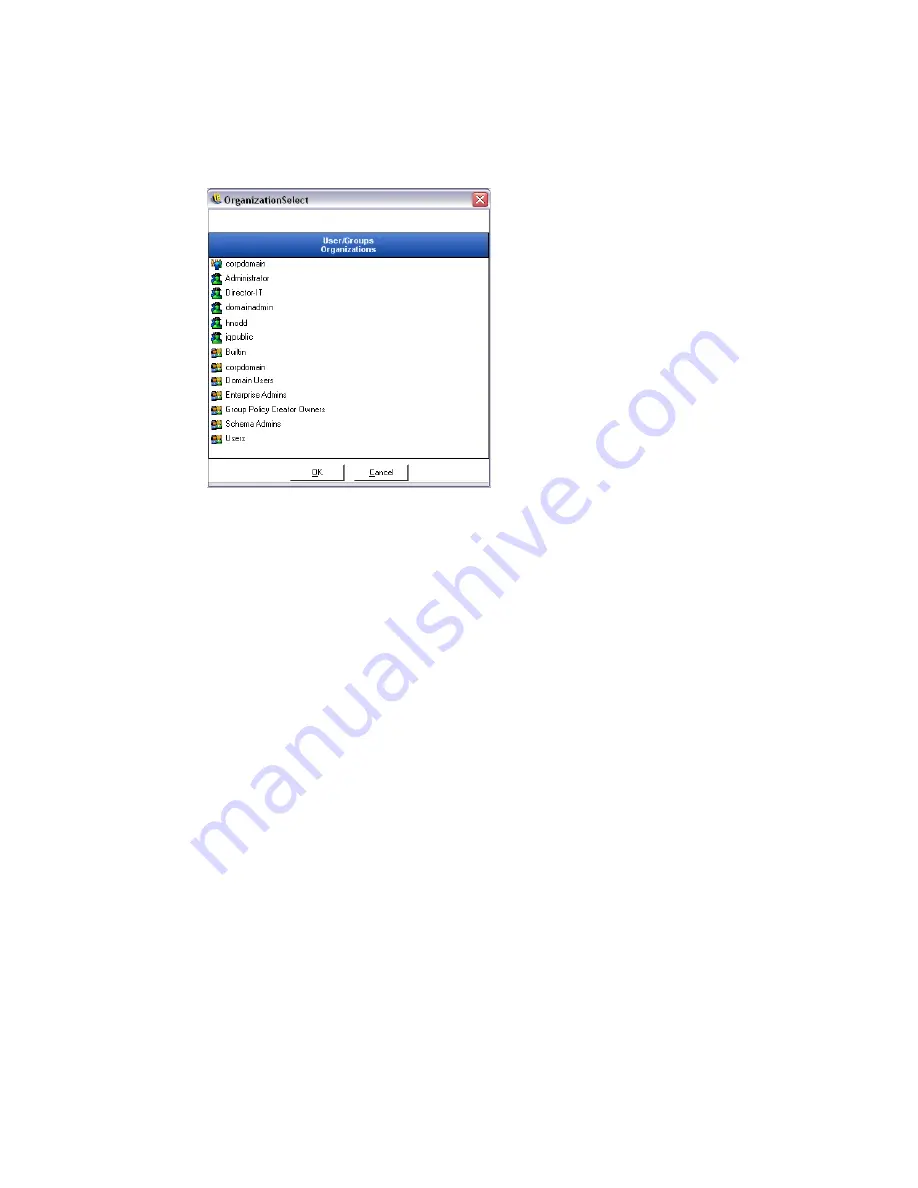
Figure 7-9
Permission Settings Organization Table
2b
Select the appropriate users and groups from the list. Use the Ctrl or Shift keys to select
multiple users.
2c
When all users and groups have been selected, click
OK
button to add the users and
groups to the grid on the Permissions form.
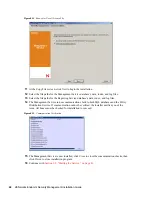
3
Assign permissions to the available users and groups.
To remove a selected user or group, select the name, then click
Remove
.
Configuring Publish To Settings
Users and groups who have
Publish Policy
checked must be assigned users or groups to publish to.
To set the Publish To Settings:
1
Click the
Publish To Settings
tab.
2
From the drop-down list, select the users and groups granted the Publish permission.
Summary of Contents for ZENWORKS ENDPOINT SECURITY MANAGEMENT 3.5
Page 4: ...4 ZENworks Endpoint Security Management Installation Guide novdocx en 17 September 2009 ...
Page 8: ...8 ZENworks Endpoint Security Management Installation Guide novdocx en 17 September 2009 ...
Page 12: ...12 ZENworks Endpoint Security Management Installation Guide novdocx en 17 September 2009 ...
Page 22: ...22 ZENworks Endpoint Security Management Installation Guide novdocx en 17 September 2009 ...
Page 24: ...24 ZENworks Endpoint Security Management Installation Guide novdocx en 17 September 2009 ...
Page 44: ...44 ZENworks Endpoint Security Management Installation Guide novdocx en 17 September 2009 ...
Page 74: ...74 ZENworks Endpoint Security Management Installation Guide novdocx en 17 September 2009 ...
Page 76: ...76 ZENworks Endpoint Security Management Installation Guide novdocx en 17 September 2009 ...