BlueGate 1000
Internal Web Server
May 8, 2001
WIDCOMM, Inc, Proprietary and Confidential
28
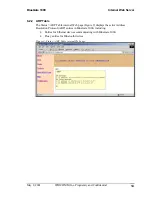
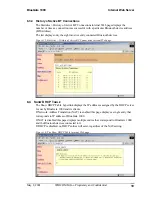
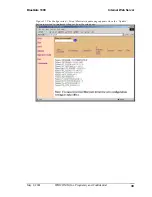
6.6.1.2.12 Authorization
Authorization is part of the process of granting or denying access to a resource. A user
name and password are required.
Computer security systems are frequently based on a two-step process:
•
Authentication ensures that a user is who he claims to be.
•
Authorization allows access to resources, based on the user's identity
If authorization is disabled, all users are allowed to connect to BlueGate 1000.
If authorization is enabled, only specific users can connect to BlueGate 1000.
See Section 6.6.1.4 for information on how to configure user authorization.
NOTE: Do not enable Authorization if the connecting device does not support security.
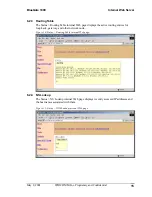
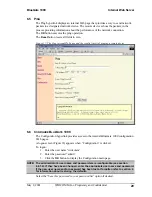
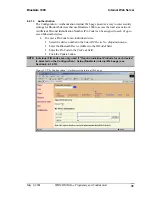
6.6.1.2.13 Authentication
Authentication is part of the process of granting or denying access to a resource.
Computer security systems are frequently based on a two-step process:
•
Authentication ensures that a user is who he claims to be.
•
Authorization allows access to resources, based on the user's identity.
Authentication, in this context, applies only to access to BlueGate 1000; it does not
necessarily permit access to any higher-level network services.
If authentication is disabled, all Bluetooth devices are allowed to connect to
BlueGate 1000.
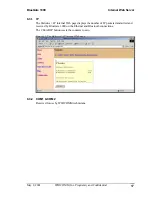
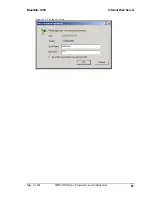
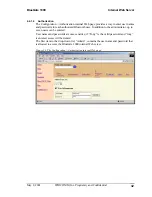
If authentication is enabled:
•
A single fixed Pin Code may be used for all devices.
•
A different Pin Code may be used for each device.
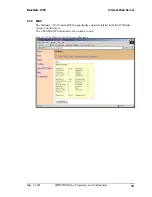
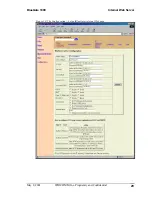
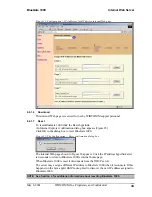
See Section 6.6.1.3 for more information on how to configure authentication.
Enabling authentication generates a link key for each device. Link keys are based on the
PIN code and the Bluetooth device address.
NOTE: Do not enable Authentication if the connecting device does not support security.