BlueGate 1000
Appendix—A, Intro to BT
May 8, 2001
WIDCOMM, Inc, Proprietary and Confidential
A-1
Appendix A—An Introduction To Bluetooth
This document provides a brief non-technical overview of Bluetooth.
For information on a specific topic click the appropriate link below:
1.
Overview
2.
Device Identity
3.
Security Introduction
a)
Authorization
b)
Authentication
c)
Encryption
d)
Service Level
4.
Bluetooth Services
5.
Device Inquiry and Service Discovery
a)
Device Inquiry
b)
Service Discovery
c)
Security
6.
A typical connection scenario
.
Overview
The term “Bluetooth” refers to a worldwide standard for the wireless exchange of data
between two devices.
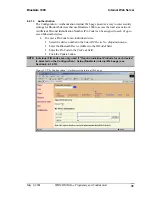
In order to exchange data, two Bluetooth devices must establish a connection.
Before a connection is established, one device must request a connection with another.
The second device accepts (or rejects) the connection.
The originator of the request is known as the
client
.
The device that accepts (or rejects) the request is known as the
server
.
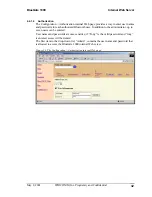
Bluetooth devices can act as both client and server.
A client Bluetooth device runs a software program that requests a connection to another
device as part of its normal operation. For example, the program may request a
connection to a remote computer, a printer, or a modem.
Becoming a Bluetooth client normally requires an action by the device operator, such as
an attempt to browse a remote computer, print a file or dial out on a modem.
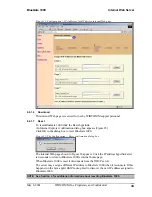
Every Bluetooth device that provides a service must be prepared to respond to a
connection request. Bluetooth software is always running in the background on the
server, ready to respond to connection requests.
<back>