©
Palo
Alto
Networks,
Inc.
Panorama
6.1
Administrator’s
Guide
•
171
Monitor
Network
Activity
Use
Case:
Respond
to
an
Incident
Using
Panorama
Review
Threat
Logs
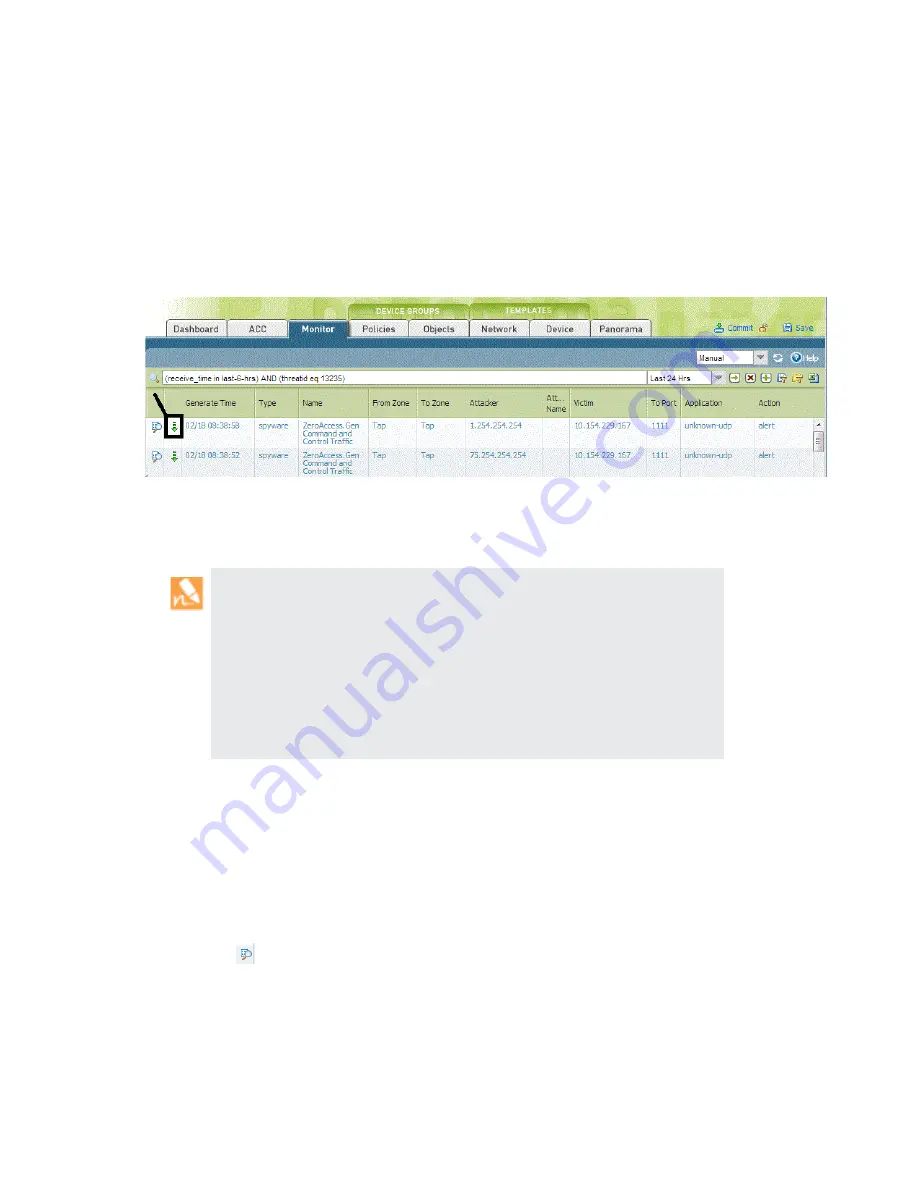
To
begin
investigating
the
alert,
use
the
threat
ID
to
search
the
threat
logs
on
Panorama
(
Monitor > Logs >
Threat
).
From
the
threat
logs,
you
can
find
the
IP
address
of
the
victim,
export
the
packet
capture
(PCAP,
has
a
green
arrow
icon
in
the
log
entry)
and
use
a
network
analyzer
tool
such
as
WireShark
to
review
the
packet
details.
In
the
HTTP
case,
look
for
a
malformed
or
bogus
HTTP
REFERER
in
the
protocol,
suspicious
host,
URL
strings,
the
user
agent,
the
IP
address
and
port
in
order
to
validate
the
incident.
Data
from
these
pcaps
is
also
useful
in
searching
for
similar
data
patterns
and
creating
custom
signatures
or
modifying
security
policy
to
better
address
the
threat
in
the
future.
As
a
result
of
this
manual
review,
if
you
feel
confident
about
the
signature,
consider
transitioning
the
signature
from
an
alert
action
to
a
block
action
for
a
more
aggressive
approach.
In
some
cases,
you
may
choose
to
add
the
attacker
IP
to
an
IP
block
list
to
prevent
further
traffic
from
that
IP
address
from
reaching
the
internal
network.
To
continue
with
the
investigation
on
the
incident,
use
the
information
on
the
attacker
and
the
victim
IP
address
to
find
out
more
information,
such
as:
Where
is
the
attacker
located
geographically?
Is
the
IP
address
an
individual
IP
address
or
a
NATed
IP
address?
Was
the
event
caused
by
a
user
being
tricked
into
going
to
a
website,
a
download,
or
was
it
sent
through
an
attachment?
Is
the
malware
being
propagated?
Are
there
other
compromised
hosts/endpoints
on
the
network?
Is
it
a
zero
‐
day
vulnerability?
The
log
details
for
each
log
entry
display
the
Related Logs
for
the
event.
This
information
points
you
to
the
traffic,
threat,
URL
filtering
or
other
logs
that
you
can
review
and
correlate
the
events
that
led
to
the
incident.
For
example,
filter
the
traffic
log
(
Monitor > Logs > Traffic
)
using
the
IP
address
as
both
the
source
and
the
destination
IP
to
get
a
complete
picture
of
all
the
external
and
internal
hosts/clients
with
which
this
victim
IP
address
has
established
a
connection.
If
you
see
a
DNS
‐
based
spyware
signature,
the
IP
address
of
your
local
DNS
server
might
display
as
the
Victim IP
address.
Often
this
is
because
the
firewall
is
located
north
of
the
local
DNS
server,
and
so
DNS
queries
show
the
local
DNS
server
as
the
source
IP
rather
than
showing
the
IP
address
of
the
client
that
originated
the
request.
If
you
see
this
issue,
enable
the
DNS
sinkholing
action
in
the
anti
‐
spyware
profile
in
security
policy
in
order
to
identify
the
infected
hosts
on
your
network.
DNS
sinkholing
allows
you
to
control
outbound
connections
to
malicious
domains
and
redirect
DNS
queries
to
an
internal
IP
address
that
is
unused;
the
sinkhole
that
does
not
put
out
a
response.
When
a
compromised
host
initiates
a
connection
to
a
malicious
domain,
instead
of
going
out
to
the
Internet,
the
firewall
redirects
the
request
to
the
IP
address
you
defined
and
it
is
sinkholed.
Now,
reviewing
the
traffic
logs
for
all
hosts
that
connected
to
the
sinkhole
allows
you
locate
all
compromised
hosts
and
take
remedial
action
to
prevent
the
spread.
















































