©
Palo
Alto
Networks,
Inc.
Panorama
6.1
Administrator’s
Guide
•
99
Manage
Firewalls
Use
Case:
Configure
Firewalls
Using
Panorama
Use
Case:
Configure
Firewalls
Using
Panorama
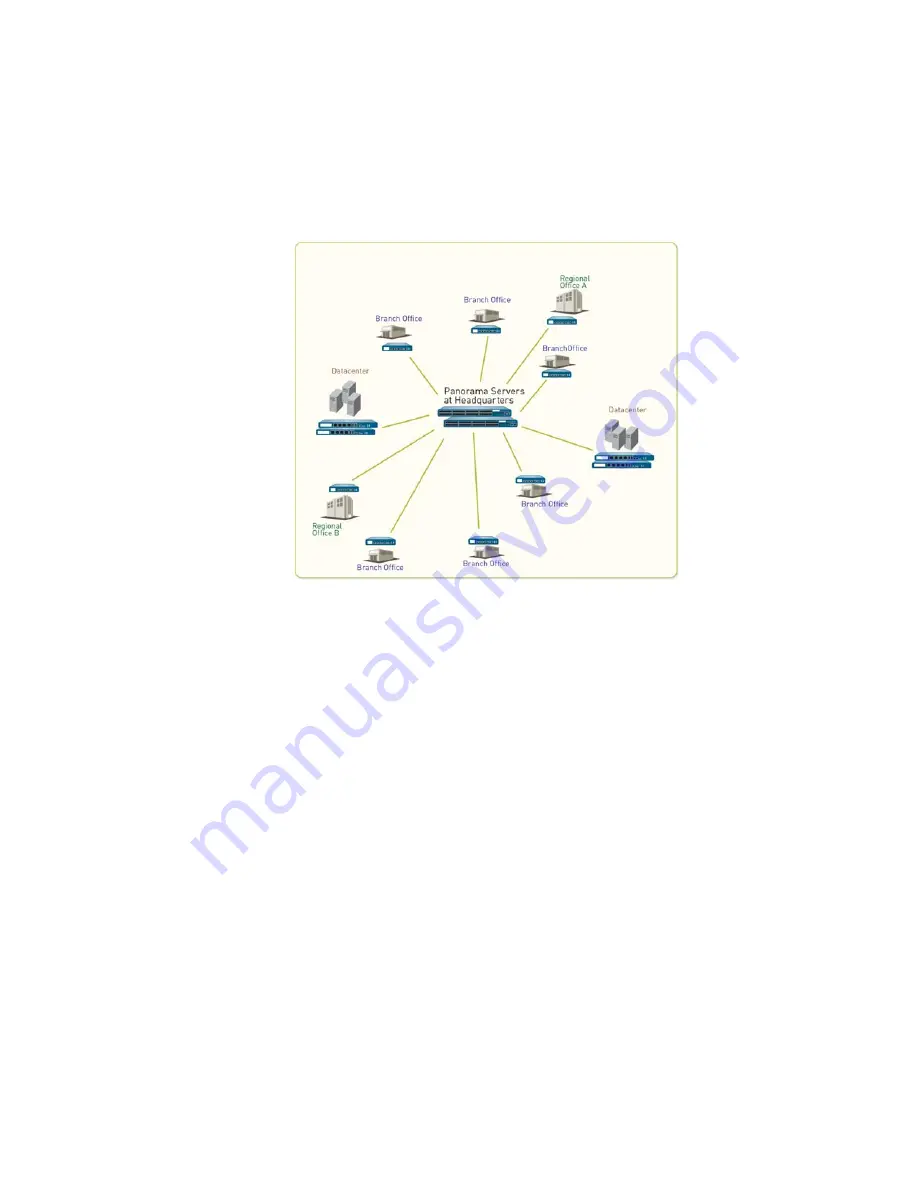
Let’s
say
that
you
want
to
use
Panorama
in
a
high
availability
configuration
to
manage
a
dozen
firewalls
on
your
network:
you
have
six
firewalls
deployed
across
six
branch
offices,
a
pair
of
firewalls
in
a
high
availability
configuration
at
each
of
two
datacenters,
and
a
firewall
in
each
of
the
two
regional
head
offices.
The
first
step
in
creating
your
central
management
strategy
is
to
determine
how
to
group
the
firewalls
into
device
groups
and
templates
to
efficiently
push
configurations
from
Panorama.
You
can
base
the
grouping
on
the
business
functions,
geographic
locations,
or
administrative
domains
of
the
firewalls.
In
this
example,
you
create
two
device
groups
and
three
templates
to
administer
the
devices
using
Panorama:
Device
Groups
In
this
example,
we
decide
to
define
two
Device
Groups
based
on
the
functions
the
firewalls
will
perform:
DG_BranchAndRegional
for
grouping
devices
that
serve
as
the
security
gateways
at
the
branch
offices
and
at
the
regional
head
offices.
We
placed
the
branch
office
firewalls
and
the
regional
office
firewalls
in
the
same
Device
Group
because
devices
with
similar
functions
will
require
similar
policy
rulebases.
DG_DataCenter
for
grouping
the
devices
that
secure
the
servers
at
the
datacenters.
We
can
then
administer
shared
policies
across
both
Device
Groups
as
well
as
administer
distinct
Device
Group
policies
for
the
regional
office
and
branch
office
groups.
Then
for
added
flexibility,
the
local
administrator
at
a
regional
or
branch
office
can
create
local
rules
that
match
specific
source,
destination,
and
service
flows
for
accessing
applications
and
services
that
are
required
for
that
office.
In
this
example,
we
create
the
following
hierarchy
for
security
policies;
you
can
use
a
similar
approach
for
any
of
the
other
rulebases:
















































