158
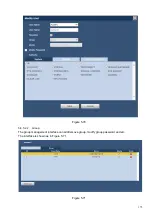
5.8.3.1.2 Tampering
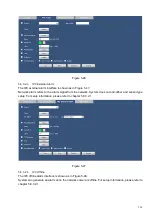
The tampering interface is shown as in Figure 5-42.
After analysis video, system can generate a camera masking alarm when the detected moving signal
reached the sensitivity you set here.
For detailed setups, please refer to chapter 5.8.3.1.1 motion detect for detailed information.
Figure 5-42
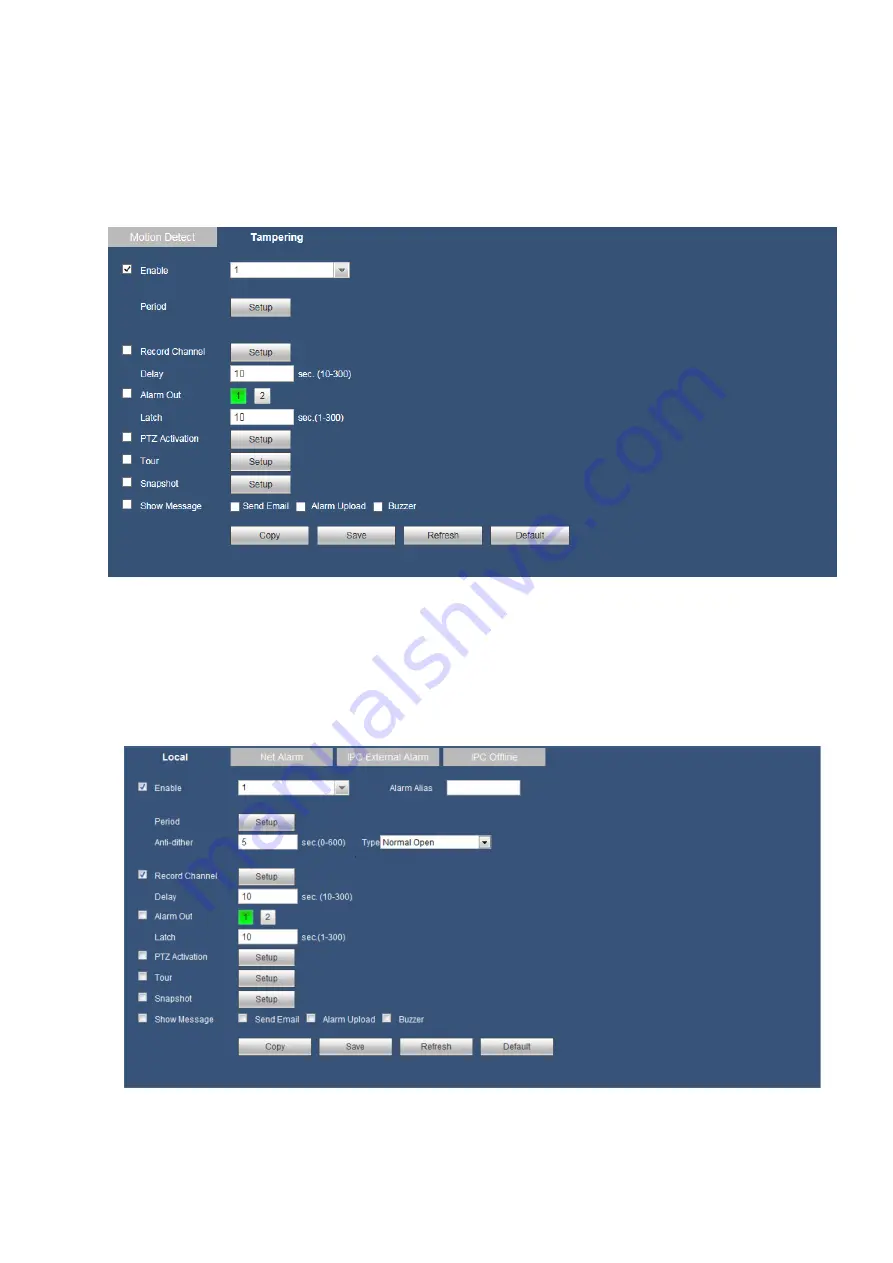
5.8.3.2 Alarm
Before operation, please make sure you have properly connected alarm devices such as buzzer. The
input mode includes local alarm and network alarm.
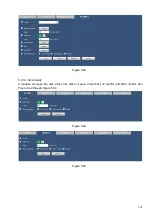
5.8.3.2.1 Alarm
The local alarm interface is shown as in Figure 5-43. It refers to alarm from the local device.
Figure 5-43
Summary of Contents for k-nl304k
Page 1: ...Network Disk Recorder User s Manual Model No K NL304K K NL308K K NL316K Version 1 0 5 ...
Page 32: ...23 The following figure is based on our K NL316K product Figure 3 2 ...
Page 50: ...41 Figure 4 25 ...
Page 67: ...58 Figure 4 52 Figure 4 53 ...
Page 88: ...79 Figure 4 71 Figure 4 72 ...
Page 89: ...80 Figure 4 73 Figure 4 74 ...
Page 94: ...85 Figure 4 78 Figure 4 79 ...
Page 95: ...86 Figure 4 80 Figure 4 81 ...
Page 96: ...87 Figure 4 82 Figure 4 83 ...
Page 99: ...90 Figure 4 86 Figure 4 87 ...
Page 114: ...105 send rate and receive rate at the top panel Figure 4 105 ...
Page 119: ...110 Figure 4 111 Figure 4 112 ...
Page 129: ...120 Figure 4 125 Figure 4 126 ...
Page 164: ...155 Figure 5 38 Figure 5 39 Figure 5 40 ...
Page 172: ...163 Figure 5 51 Figure 5 52 Figure 5 53 Figure 5 54 ...