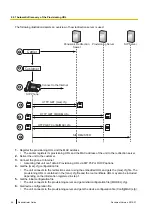
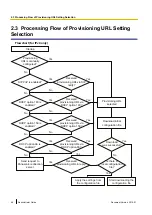
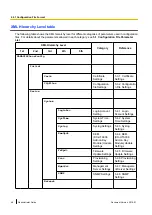
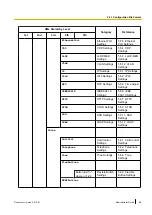
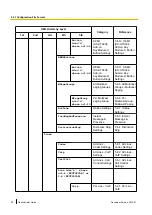
2.6 Secure Provisioning
2.6.1 Using Encryption When Transferring Configuration Files
This method involves transferring the configuration files in a encrypted format, where a symmetric key is used
to encrypt and decrypt the file.
Provisioning Server Requirements
In order to use this method, the server must be designed to comply with the following process in regards to
how the server gives the device its key and how the key is changed.
1.
The server must be capable of generating a unique 32-byte key for each device. This key is used to encrypt
the configuration files.
2.
Prior to the device's first download of its MAC-specific configuration file (known as the standard
configuration file), the server must generate a plain text MAC-specific configuration file for the device. This
is where the key is placed and how the device gets its key.
3.
After the device's first download, the server must delete the plain text MAC-specific configuration file, and
generate an encrypted version for the device configuration files using the key. The server encrypts the file
using OpenSSL and the device's key.
–
At this point, when the phone downloads the device configuration files, it will decrypt the files using the
previously obtained key.
4.
If the device ever needs a new key, there must be a method for an administrator to access the server and
generate a new key for the device. This will force the server to delete the existing encrypted configuration
files of the device and generate a new key as well as a new plain text MAC-specific configuration file. Once
the device downloads the new plain text MAC-specific configuration file, the server again deletes it and
encrypts the configuration files with the new key.
–
Devices always accept a plain text MAC-specific configuration file if the server provides one.
Note
1.
We strongly recommended that the server pass the key to the device using the standard configuration
file.
2.
Use an OpenSSL command to encrypt the configuration file and assign the file extension ".enc" to the
encrypted configuration file.
–
OpenSSL command for encrypting a file:
openssl enc -aes-128-cbc -a -salt -pass pass:
12341234abcdabcd12341234abcdabcd -in plain.txt -out encrypted.enc
–
OpenSSL command for decrypting a file:
openssl enc -d -aes-128-cbc -a -pass pass:
12341234abcdabcd12341234abcdabcd -in encrypted.enc
3.
The supported algorithms for encryption and decryption are:
AES-128-CBC, AES-196-CBC, and AES-256-CBC
4.
Use the following parameters to specify the key information in the plain text MAC-specific configuration
file.
–
CFG_FILE_KEY (see
®
Page 257): used to specify the key
–
CFG_FILE_KEY_LENGTH (see
®
Page 257): used to specify the encrypt/decrypt algorithm
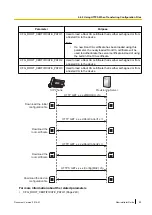
Example
This example assumes the following:
1.
The initial configuration file only specifies to use the standard configuration file.
2.
After the device downloads the initial configuration file and the standard configuration file, it detects that a
key is provided by the server.
Document Version 2015-01
Administrator Guide
57
2.6.1 Using Encryption When Transferring Configuration Files
Summary of Contents for KX-UTG200
Page 26: ...26 Administrator Guide Document Version 2015 01 Table of Contents ...
Page 62: ...62 Administrator Guide Document Version 2015 01 2 8 DHCP Provisioning ...
Page 366: ...366 Administrator Guide Document Version 2015 01 5 10 4 Log Settings Log Display ...
Page 382: ...382 Administrator Guide Document Version 2015 01 6 4 Logo and Wallpaper Settings ...
Page 390: ...390 Administrator Guide Document Version 2015 01 7 5 SSH Settings Debug Settings ...
Page 391: ...Section 8 Appendix Document Version 2015 01 Administrator Guide 391 ...
Page 398: ...398 Administrator Guide Document Version 2015 01 8 1 3 14 11 1 Software File Version 03 131 ...
Page 399: ...Index Document Version 2015 01 Administrator Guide 399 ...
Page 409: ...Document Version 2015 01 Administrator Guide 409 Notes ...
Page 410: ...410 Administrator Guide Document Version 2015 01 Notes ...
Page 411: ...Document Version 2015 01 Administrator Guide 411 Notes ...