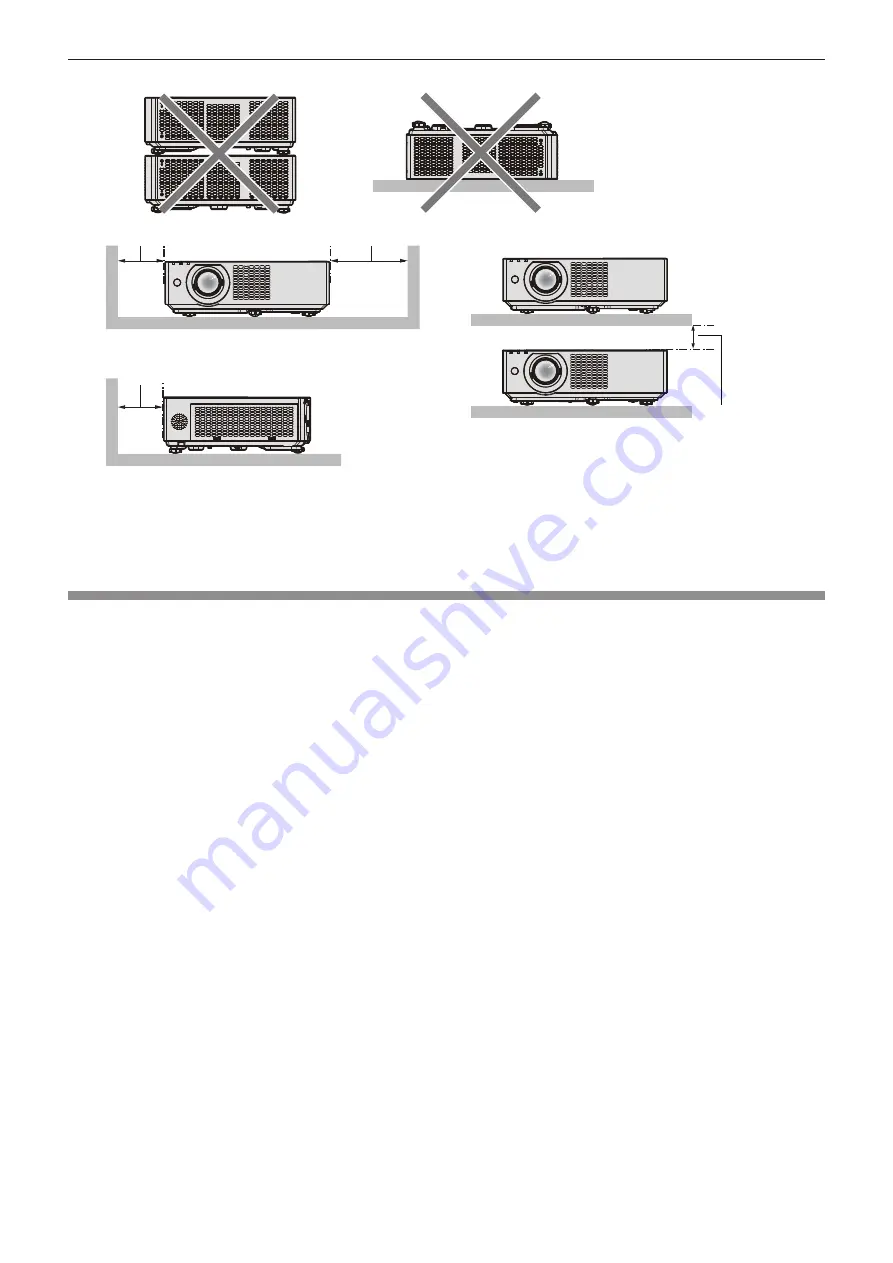
500 mm (19-11/16")
or longer
500 mm (19-11/16")
or longer
200 mm (7-7/8")
or longer
1 000 mm (39-3/8")
or longer
f
Do not install the projector in a confined space.
When placing the projector in a confined space, a ventilation and/or air conditioning system is required. Exhaust
heat may accumulate when the ventilation is not enough, triggering the protection circuit of the projector.
f
Panasonic Connect Co., Ltd. takes no responsibility for any damage to the product caused by an inappropriate
choice of location for installing the projector, even if the warranty period of the product has not expired.
Security
When using this product, take safety measures against the following incidents.
f
Personal information being leaked via this product
f
Unauthorized operation of this product by a malicious third party
f
Interfering or stopping of this product by a malicious third party
Take sufficient security measures.
f
Make your password as difficult to guess as possible.
f
Change your password periodically.
f
Panasonic Connect Co., Ltd. or its affiliate company never inquires a password directly to a customer. Do not
tell your password in case you receive such an inquiry.
f
The connecting network must be secured by firewall or others.
r
Security when using the wireless LAN product
The advantage of a wireless LAN is that information can be exchanged between a computer or other such
equipment and a wireless access point using radio waves, instead of using a LAN cable, as long as you are within
range for radio transmissions.
On the other hand, because the radio wave can travel through an obstacle (such as a wall) and is accessible from
anywhere within a given range, following problems may occur if security setting is insufficient.
f
Transmitted data may be intercepted
A malicious third party may intentionally intercept radio waves and monitor the following transmitted data.
g
Personal information such as your ID, password, credit card number
g
Content of an Email
f
Illegally accessed
A malicious third party may access your personal or corporate network without authorization and engage in the
following types of behavior.
g
Retrieve personal and/or secret information (information leak)
g
Spread false information by impersonating a particular person (spoofing)
g
Overwrite intercepted communications and issue false data (tampering)
g
Spread harmful software such as a computer virus and crash your data and/or system (system crash)
Since most wireless LAN adapters or access points are equipped with security features to take care of these
problems, you can reduce the possibility of these problems occurring when using this product by making the
ENGLISH
-
21
Chapter 1 Preparation - Precautions for use
















































