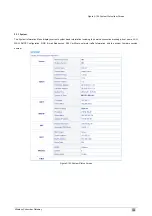
Item
Default
Description
802.1x
Disable
Enables or disables the 802.1x function.
Encryption
64 bit
The WSG-403 supports 64-bit or 128 bit 802.1x encryption.
Re-key Time
86400 Seconds Enter a number in the field to set the force re-keying interval.
Server IP
Empty
Enter the RADIUS server IP address or domain name. The
maximum allowed characters length is 15.
Authentication Port 1812
Enter the authentication port number. The allowed numbers
are from 0 to 65535.
Share Secret Key
Empty
Enter the RADIUS secret key.
Beacon Interval
200
This value valid range is 1 to 1000 indicates the frequency
interval of the beacon.
RTS Threshold
2347
This value valid range is 256-2342. This setting determines
the packet size at which the WSG-403 issues a request to
send (RTS) before sending the packet. A low RTS Threshold
setting can be useful in areas where many client devices are
associating with the WSG-403, or in areas where the clients
are far apart and can detect only the WSG-403 and not each
other.
Fragmentation
Threshold
2432
This setting determines the size at which packets are
fragmented. Enter a setting ranging from 256 to 2432 bytes.
Use a low setting in areas where communication is poor or
where there is a great deal of radio interference.
Preamble Type
Long Preamble
The preamble type is a section of data at the head of a packet
that contains information the WSG-403 and client devices
need when sending and receiving packets. The setting menu
allows you to select a long, short or dynamic preamble type.
Authentication
Method
Open System
Select open system, shared Key or both.
Open System—
Allows any device to authenticate and then
attempt to communicate with the WSG-403. Using open
authentication, any wireless device can authenticate with the
WSG-403, but the device can only communicate if its WEP
keys match the WSG-403. Devices not using WEP do not
attempt to authenticate with a Wireless Service Gateway that
is using WEP.
Shared Key—
During shared key authentication, the
WSG-403 sends an unencrypted challenge text string to any
device attempting to communicate with the WSG-403. The
device-requesting authentication encrypts the challenge text
and sends it back to the WSG-403. If the challenge text is
encrypted correctly, the WSG-403 allows the requesting
device to authenticate. Both the unencrypted challenge and
the encrypted challenge can be monitored, however, which
leaves the WSG-403 open to attack from an intruder who
calculates the WEP key by comparing the unencrypted and
encrypted text strings. Because of this weakness, shared key
authentication can be less secure than open authentication.
Both—
With this setting wireless stations can communicate
with or without data encryption.
WSG-403 User Guide
106
Summary of Contents for Hot Spot WSG-403
Page 1: ...Hot Spot Wireless Subscriber Gateway WSG 403 User s Manual ...
Page 2: ......
Page 4: ...WSG 403 User Guide 2 ...
Page 36: ...Figure 3 30 System Setting Screen Figure 3 31 System Setting Screen WSG 403 User Guide 34 ...
Page 57: ...Figure 3 65 Example 2 Amount 7 x 1 7 00 Wireless Subscriber Gateway 55 ...
Page 66: ...Figure 3 77 3 2 9 Keypad WSG 403 User Guide 64 ...