MH-5001 User Manual
Chapter 14
Virtual Private Network –Dynamic IPSec
116
Chapter 14
Virtual Private Network –Dynamic IPSec
This chapter introduces Dynamic IPSec VPN and explains how to implement it.
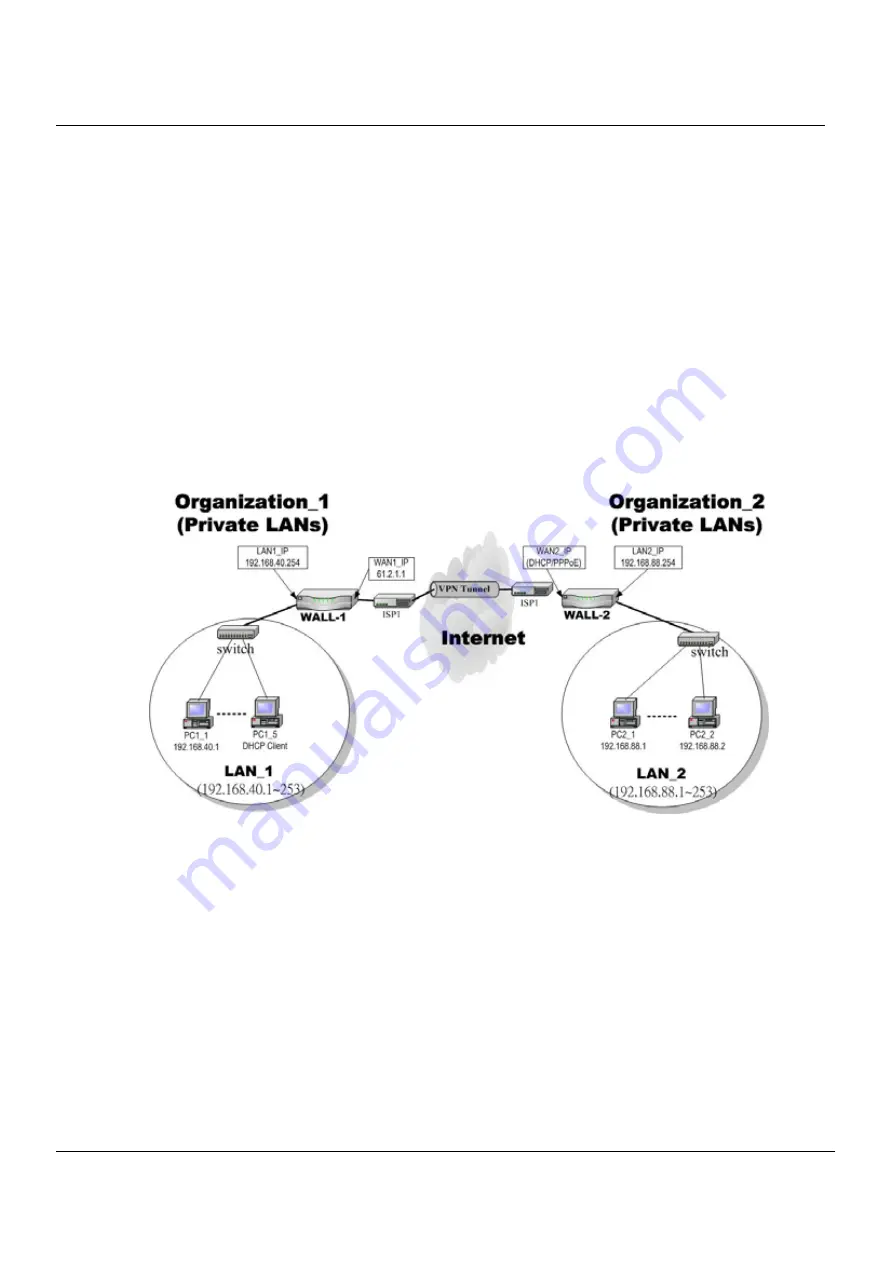
As described in the Figure 2-1, we will extend to explain how to make a dynamic VPN link between LAN_1 and LAN_2 in this
chapter. The following Figure 14-1 is the real structure in our implemented process.
14.1 Demands
1.
When a branch office subnet LAN_1 wants to connect with another branch office subnet LAN_2 through the public
Internet instead of the expensive private leased lines, VPN can provide encryption and authentication to secure the tunnel
that connects these two LANs. If the remote VPN peer has a dynamically assigned IP address (DHCP or PPPoE) like
Organization_2, we have to use the Dynamic IPSec for the tunnel connection.
Figure 14-1 Organization_1 LAN_1 is making dynamic VPN tunnel with Organization_2 LAN_2
14.2 Objectives
1.
Let the users in LAN_1 and LAN_2 share the resources through a secure channel established using the dynamic IPSec
VPN.
14.3 Methods
1.
Separately configure WALL-1 and WALL-2 which are the edge gateways of LAN_1 and LAN_2 respectively.
















































