MH-5001 User Manual
Chapter 29
System Maintenance
211
29.5 Steps for Factory Reset
29.5.1 Step for factory reset under web GUI
Step 1.
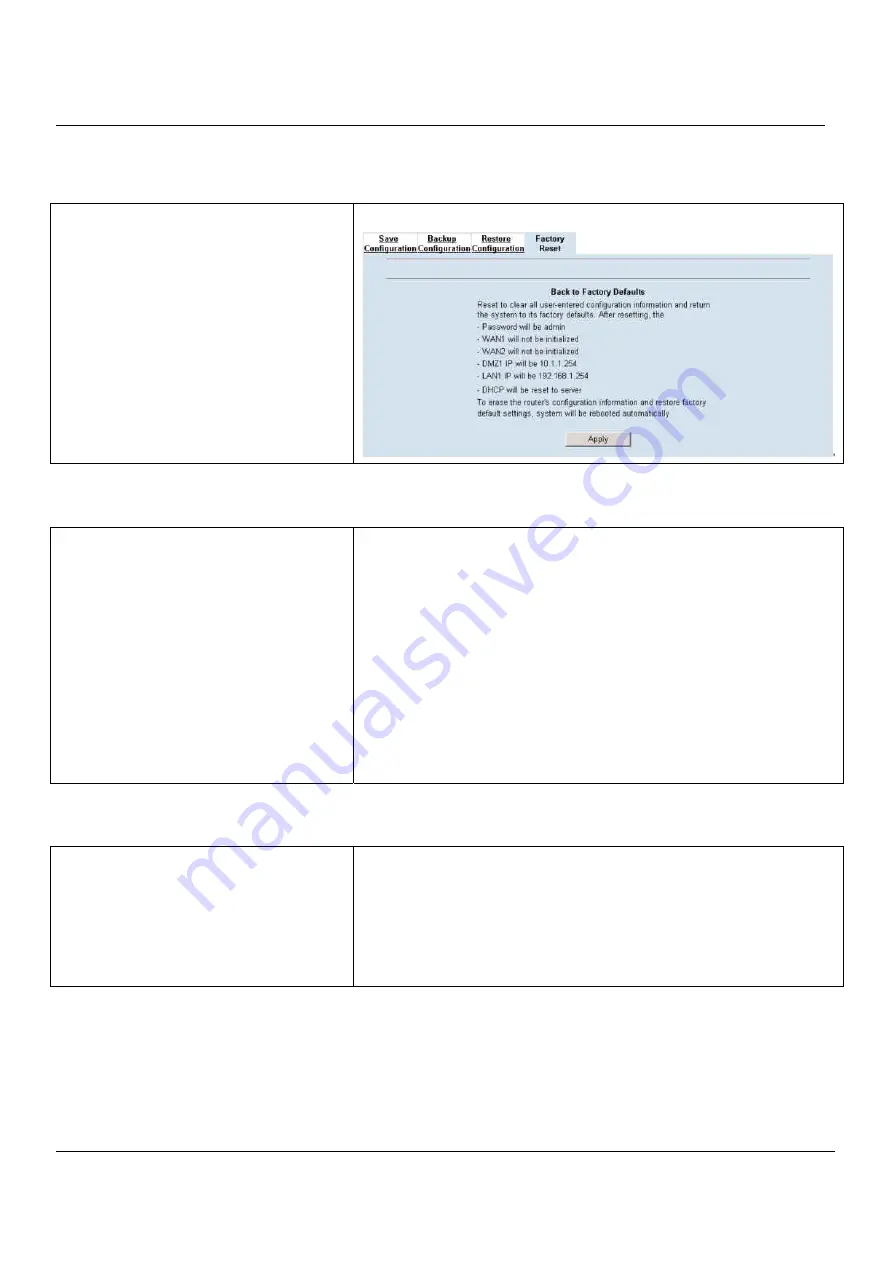
Factory reset
In the Web GUI mode. Follow the path of right
side. We can make MH-5001 configuration
restored to the factory defaults with simply
clicking the
Apply
button.
Warning: Be careful to use this function. It will
make all your present configurations disappear.
And the configuration will restore to the factory
default.
SYSTEM TOOLS > System Utilities > Factory Reset
29.5.2 Step for NORMAL factory reset
Step 1.
Factory reset
In the CLI mode. Enter
sys resetconf now
to
reset the firmware to factory default. Then the
system will reboot automatically.
NetOS/i386 (MH-5001) (tty00)
login: admin
Password:
Welcome to MH-5001 Multi-Homing Security Gateway
MH-5001> en
MH-5001# sys resetconf now
Resetting Configuration to default... DONE
System will reboot now
syncing disks... done
rebooting...
29.5.3 Steps for EMERGENT factory reset
Step 1.
Enter the boot loader
If the original firmware is damaged, you may need
to recover the firmware with the factory default.
Press
<tab>
or
<space>
during the 2-second
countdown process.
>> NetOS Loader (i386), V1.5 (Fri Feb 20 10:25:11 CST 2004)
Press <TAB> to prompt - starting in 0
Type "boot rescue" to load safe-mode kernel to
(1) rescue corrupted firmware
(2) reset password for admin
type "?" or "help" for help.
>
















































