Detecting Intrusions
When the system detects a possible network intrusion, it logs an entry to the security log.
The Enable Network Intrusion Detection System (NIDS) setting controls the logging behavior. The
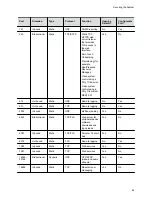
security log prefix identifies the type of packet detected, as shown in the following table:
Prefix
Packet Type
SECURITY: NIDS/unknown_tcp
Packet that attempts to connect or probe a closed TCP
port
SECURITY: NIDS/unknown_udp
Packet that probes a closed UDP port
SECURITY: NIDS/invalid_tcp
TCP packet in an invalid state
SECURITY: NIDS/invalid_icmp
ICMP or ICMPv6 packet in an invalid state
SECURITY: NIDS/unknown
Packet with an unknown protocol number in the IP
header
SECURITY: NIDS/flood
Stream of ICMP or ICMPv6 ping requests or TCP
connections to an opened TCP port
Following the message prefix, the security log entry includes the time stamp and the IP, TCP, UDP, ICMP,
or ICMPv6 headers. For example, the following security log entry shows an
unknown_udp
intrusion:
2009-05-08 21:32:52 WARNING kernel: SECURITY: NIDS/unknown_udp IN=eth0
OUT= MAC=00:e0:db:08:9a:ff:00:19:aa:da:11:c3:08:00 SRC=172.18.1.80
DST=172.18.1.170 LEN=28 TOS=0x00 PREC=0x00 TTL=63 ID=22458 PROTO=UDP
SPT=1450 DPT=7788 LEN=8
PKI Certificates
If your organization uses a public key infrastructure (PKI) for securing network connections, Poly
recommends that you have a strong understanding of certificate management and how it applies to your
system.
PKI certificates authenticate secure network connections to and from the system. The system uses
standard PKI techniques to configure and manage certificates and certificate signing requests (CSRs).
ANSI X.509 standards regulate the certificate characteristics.
Your system can generate CSRs to send to a certificate authority (CA), a trusted entity that validates and
officially issues, or signs, PKI certificates. Your system uses those certificates for client and server
authentication.
If your system is in an environment without PKI, you don’t need a CA-signed certificate; the system
comes with a self-signed certificate for its TLS connections. When you deploy PKI, however, self-signed
certificates aren’t trusted and you must use CA-signed certificates.
Securing the System
51