Pause limit out [frame]
Value limits the number of continuous Pause refresh frames that can be transmitted from this port
– assuming each Pause refresh is for the maximum pause time of 65536 slot times. When full-duplex
Flow Control is enabled on this port, this parameter is used to limit the number of Pause refresh
frames that can be generated from this port to keep this port’s link partner from sending any data.
Clearing this parameter to 0 will allow continuous Pause frame refreshes to egress this port as long
as this port remains congested.
Setting this parameter to 1 will allow 1 Pause frame to egress from this port for each congestion
situation.
Setting this parameter to 2 will allow up to 2 Pause frames to egress from this port for each conges-
tion situation, etc.
Ignore checksum
Enables ignoring Frame checksum (FCS) - or in other words - Force good FCS in the frame. When
this parameter is not set (default behavior), frames entering this port must have a good CRC or
else they are discarded. When this parameter is set, the last four bytes of frames received on this
port are overwritten with a good CRC and the frames are accepted by the switch (assuming that
the frame’s length is good and it has a destination).
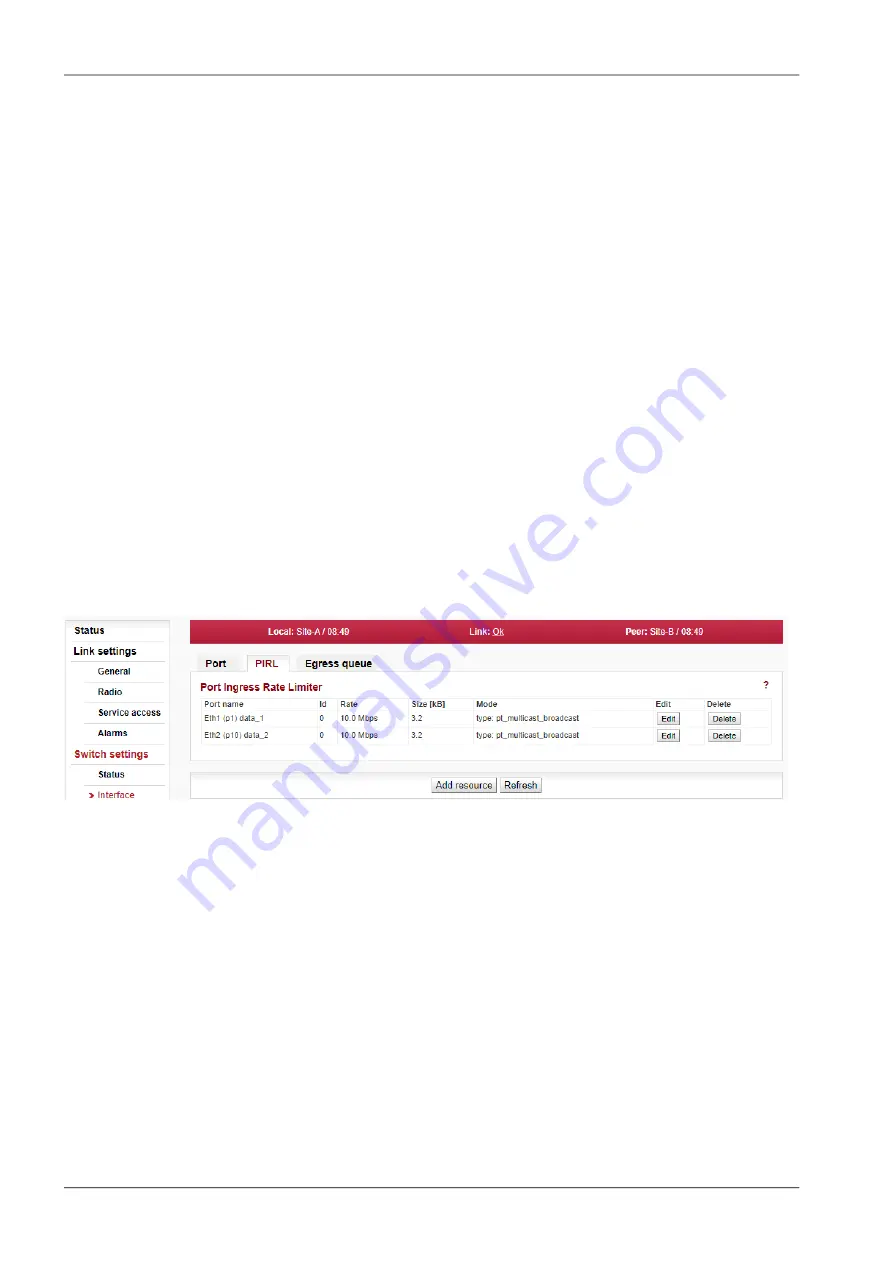
5.5.2.2. PIRL
Page allows to configure PIRL -
Port-based Ingress Rate Limiter
.
It is a useful feature to limit bursts and storms of packets according different services, priorities and
other network parameters to optimize the usage of limited capacity of wireless link.
Fig. 5.21: Menu Switch settings > Interface > PIRL
The device supports per port TCP/IP ingress rate limiting along with independent Storm prevention.
Port based ingress rate limiting accommodates information rates from 64 Kbps to 1 Mbps in increments
of 64 Kbps, from 1 Mbps to 100 Mbps in increments of 1 Mbps and from 100 Mbps to 1000 Mbps in
increments of 10 Mbps.
In addition to this, the device supports Priority based ingress rate limiting. Given ingress rate resource
can be configured to track any of the four priority traffic types. The device supports a color- blind leaky
bucket scheme, one of the popular schemes for implementing rate limiting. The way a leaky bucket
scheme works is that the bucket drains tokens constantly at a rate called Committed Information Rate
(CIR) and the bucket gets replenished with tokens whenever a frame is allowed to go through the
bucket. All calculations for this bucket are done in tokens. Therefore, both bucket decrementing and
incrementing is performed using tokens (i.e. frame bytes are converted into bucket tokens for calculation
purposes).
RAy3 Microwave Link – © RACOM s.r.o.
120
Configuration
Summary of Contents for RAy3-11
Page 2: ......
















































