DefensePro User Guide
Security Configuration
168
Document ID: RDWR-DP-V0602_UG1201
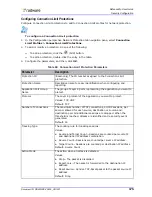
Configuring BDoS Profiles for Network Protection
When you configure Behavioral DoS profiles, you need to configure the bandwidth and quota
settings. Setting the bandwidth and quota values properly and accurately is important, because
initial baselines and attack detection sensitivity are based on these values.
Recommended settings for policies that include Behavioral DoS profiles are as follows:
•
Configure rules containing Behavioral DoS profiles using Networks with source = Any, the public
network, and destination = Protected Network. It is recommended to create multiple Behavioral
DoS rules, each one protecting a specific servers segment (for example, DNS servers segment,
Web server segments, Mail servers segments, and so on). This assures optimized learning of
normal traffic baselines.
•
It is not recommended to define a network with the Source and Destination set to Any, because
the device collects statistics globally with no respect to inbound and outbound directions. This
may result in lowered sensitivity to detecting attacks.
•
When a rule’s Direction is set to One Way, the rule prevents incoming attacks only. When a rule’s
Direction is set to Two Way, the rule prevents both incoming and outgoing attacks. In both
cases, the traffic statistics are collected for incoming and outgoing patterns to achieve optimal
detection.
You can configure footprint bypass to bypass specified footprint types or values. For more
information, see
Configuring BDoS Footprint Bypass, page 124
To configure a BDoS profile
1. In the Configuration perspective Network Protection tab navigation pane, select BDoS Profiles.
2. Do one of the following:
—
To add a profile, click the
(Add) button.
—
To edit a profile, double-click the entry in the table.
3. Configure the parameters; and then, and click OK.
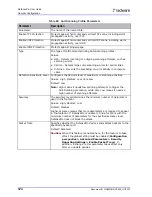
Table 87: BDoS Profile Parameters
Parameter
Description
Profile Name
The name of the BDoS profile.
Enable Transparent
Optimization
Specifies whether transparent optimization is enabled.
Some network environments are more sensitive to dropping packets (for
example, VoIP), therefore it is necessary to minimize the probability that
legitimate traffic is dropped by the IPS device. This transparent
optimization can occur during BDoS’s closed-feedback iterations until a
final footprint is generated.
Note:
When transparent optimization is enabled, the profile does not
mitigate the attack until the final footprint is generated, which
takes several seconds.
Summary of Contents for DefensePro 6.02
Page 1: ...DefensePro User Guide Software Version 6 02 Document ID RDWR DP V0602_UG1201 January 2012 ...
Page 2: ...DefensePro User Guide 2 Document ID RDWR DP V0602_UG1201 ...
Page 20: ...DefensePro User Guide 20 Document ID RDWR DP V0602_UG1201 ...
Page 28: ...DefensePro User Guide Table of Contents 28 Document ID RDWR DP V0602_UG1201 ...
Page 116: ...DefensePro User Guide Device Network Configuration 116 Document ID RDWR DP V0602_UG1201 ...
Page 302: ...DefensePro User Guide Real Time Security Reporting 302 Document ID RDWR DP V0602_UG1201 ...
Page 308: ...DefensePro User Guide Administering DefensePro 308 Document ID RDWR DP V0602_UG1201 ...
Page 324: ...DefensePro User Guide Troubleshooting 324 Document ID RDWR DP V0602_UG1201 ...