DefensePro User Guide
Security Configuration
Document ID: RDWR-DP-V0602_UG1201
173
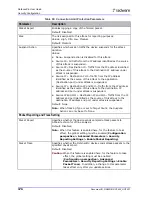
Configuring Anti-Scanning Trusted Ports
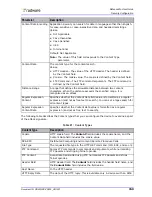
You can configure a list of Layer 4 ports on which scanning is allowed. That is, when Anti-Scanning is
enabled, there is no blocking of scans that target these ports. By default, DefensePro ignores port
113 activity.
To configure Anti-Scanning trusted ports
1. In the Configuration perspective Network Protection tab navigation pane, select Anti-Scanning
Profiles > Anti-Scanning Trusted Ports.
2. To view the trusted ports for a profile, select the profile and click Go.
3. To add a trusted port for the selected profile, click the
(Add) button.
4. Enter the Layer 4 trusted port on which scanning is allowed. Values: 1–65,535.
5. Click OK.
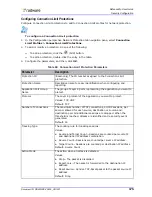
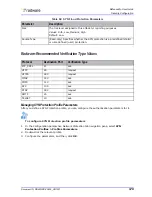
Configuring Connection Limit Profiles for Network Protection
Connection Limit profiles defend against session-based attacks, such as half open SYN attacks,
request attacks, and full connection attacks.
Connection Limit profiles contain attack definitions for groups of TCP or UDP application ports.
DefensePro counts the number of TCP connections, or UDP sessions, opened per client, per server,
or per client plus server combination, for traffic that matches a Connection Limit policy attack
definition. Once the number of connections per second reaches the specified threshold, any session/
connection over the threshold is dropped, unless the action mode defined for this attack is Report
Only.
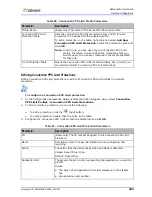
You can also define whether to suspend the source IP address, dropping traffic from this source for a
number of seconds as per Suspend Table definitions.
Recommended settings for policies that include Connection Limit profiles:
•
Configure policies containing Connection Limit profiles using Networks only with source = Any,
the public network, and destination = Protected Network. You can define segments using VLAN
tag, MPLS RDs, and physical ports.
•
It is not recommended to define networks when the Source and Destination are set to Any.
•
Policies containing Connection Limit profiles can be configured with Direction set to either One
Way or Two Way.
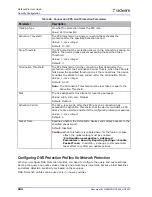
Before you configure a Connection Limit profile, ensure the following:
•
Connection Limit protection is enabled (under the Security Settings tab).
•
The Session table Lookup Mode is Full Layer 4. For more information, see
.
•
(Recommended) The required Connection Limit protections are configured. For more
information, see
Configuring Connection Limit Protections, page 175
.
Summary of Contents for DefensePro 6.02
Page 1: ...DefensePro User Guide Software Version 6 02 Document ID RDWR DP V0602_UG1201 January 2012 ...
Page 2: ...DefensePro User Guide 2 Document ID RDWR DP V0602_UG1201 ...
Page 20: ...DefensePro User Guide 20 Document ID RDWR DP V0602_UG1201 ...
Page 28: ...DefensePro User Guide Table of Contents 28 Document ID RDWR DP V0602_UG1201 ...
Page 116: ...DefensePro User Guide Device Network Configuration 116 Document ID RDWR DP V0602_UG1201 ...
Page 302: ...DefensePro User Guide Real Time Security Reporting 302 Document ID RDWR DP V0602_UG1201 ...
Page 308: ...DefensePro User Guide Administering DefensePro 308 Document ID RDWR DP V0602_UG1201 ...
Page 324: ...DefensePro User Guide Troubleshooting 324 Document ID RDWR DP V0602_UG1201 ...