DefensePro User Guide
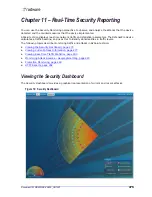
Real-Time Security Reporting
Document ID: RDWR-DP-V0602_UG1201
289
DNS Flood Attack Details
Parameter
Description
Global
Attack Characteristics
The attack characteristics comprise the following parameters:
•
Source L4 Port
•
Protocol
•
Physical Port
•
Packet Count
•
VLAN
•
MPLS RD
•
Device IP
•
Bandwidth [Kbits]
•
TTL
•
IP ID Number
•
Destination IP
•
DNS ID
•
DNS Query Count
•
L4 Checksum
•
Packet Size
•
Destination Ports
•
DNS Query
•
DNS An Query Count
Note:
Some fields can display multiple values, when relevant and
available. The values displayed depend on the current stage
of the attack. If a field is part of the dynamic signature (that
is, a specific value or values appear in all the attack traffic),
the Attack Characteristics field displays the relevant value or
values.
Attack Info
The attack information comprises the State parameter, which indicates
the state of the protection process.
Values:
•
Footprints Analysis—Behavioral DoS Protection has detected an
attack and is currently determining an attack footprint.
•
Blocking—Behavioral DoS Protection is blocking the attack based
on the attack footprint created. Through a closed feedback loop
operation, the Behavioral DoS Protection optimizes the footprint
rule, achieving the narrowest effective mitigation rule.
•
Non-attack—Nothing was blocked because the traffic was not an
attack—no footprint was detected or the blocking strictness level
was not met.
Sampled Data
Opens the Sampled Data dialog box, which contains a data on sampled
attack packets.
Footprint
Footprint Blocking Rule
The footprint blocking rule generated by the Behavioral DoS Protection,
which provides the narrowest effective blocking rule against the flood
attack.
Attack Statistics Table
This table displays attack traffic (Anomaly) and normal traffic information. Red indicates real-time
values identified as suspicious in the 15 seconds prior to when the attack was triggered. Black
indicates the learned normal traffic baselines. Table columns are displayed according to the DNS
query types: A, MX, PTR, AAAA, Text, SOA, NAPTR, SRV, Other.
Attack Statistics Graph
The graph displays a snapshot of the relevant traffic type for the 15-second period during which the
attack was triggered. For example, during a UDP flood, just UDP traffic is represented. The blue line
represents the normal adapted traffic baseline.
Summary of Contents for DefensePro 6.02
Page 1: ...DefensePro User Guide Software Version 6 02 Document ID RDWR DP V0602_UG1201 January 2012 ...
Page 2: ...DefensePro User Guide 2 Document ID RDWR DP V0602_UG1201 ...
Page 20: ...DefensePro User Guide 20 Document ID RDWR DP V0602_UG1201 ...
Page 28: ...DefensePro User Guide Table of Contents 28 Document ID RDWR DP V0602_UG1201 ...
Page 116: ...DefensePro User Guide Device Network Configuration 116 Document ID RDWR DP V0602_UG1201 ...
Page 302: ...DefensePro User Guide Real Time Security Reporting 302 Document ID RDWR DP V0602_UG1201 ...
Page 308: ...DefensePro User Guide Administering DefensePro 308 Document ID RDWR DP V0602_UG1201 ...
Page 324: ...DefensePro User Guide Troubleshooting 324 Document ID RDWR DP V0602_UG1201 ...