Document ID: RDWR-DP-V0602_UG1201
335
Appendix E – Glossary
This glossary is a list of terms and definitions used in the Radware technical environment. Some of
the words belong to the public domain, and some are Radware-specific, but all are used in the
Radware documentation.
A Radware glossary is intended to be a list of specialized words with their definitions that are used in
the Radware technical environment. Some of the words belong to the public domain, and some are
Radware-specific, but all are used in the Radware documentation, whether hardcopy or online.
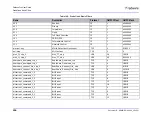
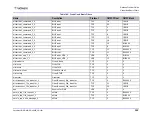
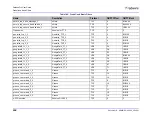
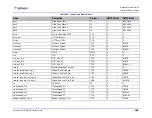
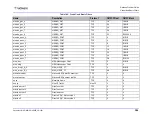
Term
Definition
Anomaly
An anomaly is unusual or unexpected behavior of traffic patterns or a
protocol.
Attack
An Attack, with an upper-case letter “A” is a realization of a threat, a
malicious action taken against a network, host or service.
Attack List
An Attack List is a database of known attackers as defined in the
Signatures Database.
Attack Signature
Database
Radware’s Attack signature database contains signatures of known
attacks.
These signatures are included in the predefined groups and profiles
supplied by Radware to create protection policies in the Connect and
Protect Table. Each attack group consists of attack signatures with
common characteristics intended to protect a specific application or range
of IPs.
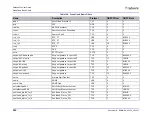
Behavioral DoS (BDoS)
Behavioral DoS (Behavioral Denial of Service) protection defends
networks from zero day network-flood attacks that jam available network
bandwidth with spurious traffic, denying use of network resources for
legitimate users.
BDoS profiles do this by identifying the footprint of the anomalous traffic.
Network-flood protection types include:
•
SYN Flood
•
TCP Flood, including TCP Fin + Ack Flood, TCP Reset Flood
•
TCP Syn + Ack Flood, TCP Fragmentation Flood
•
UDP Flood
•
ICMP Flood
•
IGMP Flood
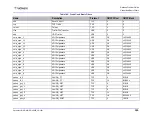
Black List
A Black List defines the IP addresses that are always blocked without
inspection.
Black lists are used as exceptions for security policies/rules, blocking all
traffic generated by IP addresses in the Black List.
Summary of Contents for DefensePro 6.02
Page 1: ...DefensePro User Guide Software Version 6 02 Document ID RDWR DP V0602_UG1201 January 2012 ...
Page 2: ...DefensePro User Guide 2 Document ID RDWR DP V0602_UG1201 ...
Page 20: ...DefensePro User Guide 20 Document ID RDWR DP V0602_UG1201 ...
Page 28: ...DefensePro User Guide Table of Contents 28 Document ID RDWR DP V0602_UG1201 ...
Page 116: ...DefensePro User Guide Device Network Configuration 116 Document ID RDWR DP V0602_UG1201 ...
Page 302: ...DefensePro User Guide Real Time Security Reporting 302 Document ID RDWR DP V0602_UG1201 ...
Page 308: ...DefensePro User Guide Administering DefensePro 308 Document ID RDWR DP V0602_UG1201 ...
Page 324: ...DefensePro User Guide Troubleshooting 324 Document ID RDWR DP V0602_UG1201 ...