DefensePro User Guide
Security Configuration
192
Document ID: RDWR-DP-V0602_UG1201
Configuring HTTP Flood Profiles for Server Protection
HTTP Flood profiles defend the applications in your network against server flooding.
Server flood attacks are aimed at specific servers causing denial of service at the server level. These
types of attacks disrupt a server by sending more requests than the server can handle, thereby
preventing access to a service.
Server attacks differ from network-flood attacks either in the attack volume or in the nature of the
requests used in the attack. Server flood attacks use legitimate requests that cannot be
distinguished from regular customer requests.
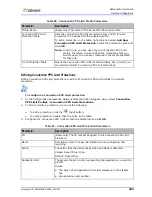
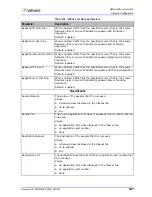
Sensitivity
The detection sensitivity of module. The sensitivity level defines thresholds for
the number and frequency of server-side error messages. These messages are
tracked for attack detection. High sensitivity specifies that the device needs few
cracking attempts to trigger the protection. Minor sensitivity specifies that the
device needs a very high number of attempts.
Values: High, Medium, Low, Minor
Default: Medium
Note:
If you are protecting a Web server that is not maintained or not
updated, it may generate HTTP-error replies at an abnormal rate, which
the device will falsely identify as an attack. In such a case, set the
sensitivity to Low.
Action Mode
The action that the device takes when an attack is detected.
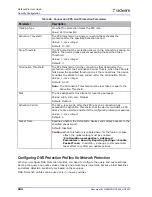
Direction
The direction of the traffic to inspect. A protection may include attacks that
should be searched only for traffic from client to server or only on traffic from
server to client.
Values:
•
Inbound—The Protection inspects traffic from policy Source to policy
Destination.
•
Outbound—The Protection inspects traffic from policy Destination to policy
Source
•
Inbound & Outbound—The Protection inspects all traffic between policy
Source to policy Destination
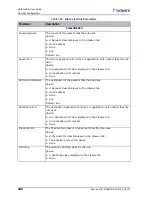
Suspend Action Specifies what traffic to suspend for a period of time.
Values:
•
None—Suspend action is disabled for this attack.
•
SrcIP—All traffic from the IP address identified as the source of the attack is
suspended.
•
SrcIP, DestIP—Traffic from the IP address identified as the source of the
attack to the destination IP address under attack is suspended.
•
SrcIP, DestPort—Traffic from the IP address identified as source of the attack
to the application (destination port) under attack is suspended.
•
SrcIP, DestIP, DestPort—Traffic from the IP address identified as the source
of the attack to the destination IP and port under attack is suspended.
•
SrcIP, DestIP, SrcPort, DestPort—Traffic from the IP address and port
identified as the source of the attack to the destination IP and port under
attack is suspended.
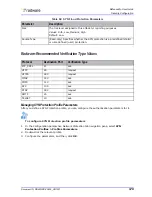
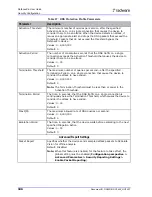
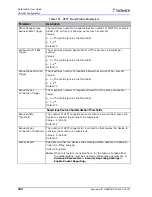
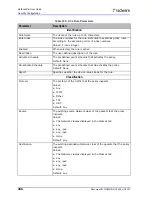
Table 100: Radware-defined Server Cracking Protections
Parameter
Description
Summary of Contents for DefensePro 6.02
Page 1: ...DefensePro User Guide Software Version 6 02 Document ID RDWR DP V0602_UG1201 January 2012 ...
Page 2: ...DefensePro User Guide 2 Document ID RDWR DP V0602_UG1201 ...
Page 20: ...DefensePro User Guide 20 Document ID RDWR DP V0602_UG1201 ...
Page 28: ...DefensePro User Guide Table of Contents 28 Document ID RDWR DP V0602_UG1201 ...
Page 116: ...DefensePro User Guide Device Network Configuration 116 Document ID RDWR DP V0602_UG1201 ...
Page 302: ...DefensePro User Guide Real Time Security Reporting 302 Document ID RDWR DP V0602_UG1201 ...
Page 308: ...DefensePro User Guide Administering DefensePro 308 Document ID RDWR DP V0602_UG1201 ...
Page 324: ...DefensePro User Guide Troubleshooting 324 Document ID RDWR DP V0602_UG1201 ...