C
HAPTER
10:
G
ENERATING
R
EPORTS
119
Chapter 10: Generating Reports
Reports can be sorted by clicking on the column headers. Click a column header to sort report
data by the values in that column. The data will refresh in ascending order alphabetically,
numerically, or chronologically. Click the column header again to sort in descending order.
You can resize the column width in all reports. Hold your mouse pointer on the column divider in
the header row until the pointer becomes a double-headed arrow. Click and drag the arrow to the
left or right to adjust column width.
The sorting value and column width you use becomes the default report view the next time you
log in and run CC-SG reports. For all reports, you can double-click a row to view further details
of the report.
Note: In all reports, use CTRL+click to deselect a highlighted row.
Audit Trail Report
The
Audit Trail
report displays audit logs and access in CC-SG. It captures actions such as
adding, editing, or deleting devices or ports, and other modifications.
CC-SG maintains an Audit Trail of the following events:
•
When CC-SG is launched
•
When CC-SG is stopped
•
When a user logs on CC-SG
•
When a user logs off CC-SG
•
When a user starts a node connection
1.
On the
Reports
menu, click
Audit Trail.
The
Audit Trail
screen appears.
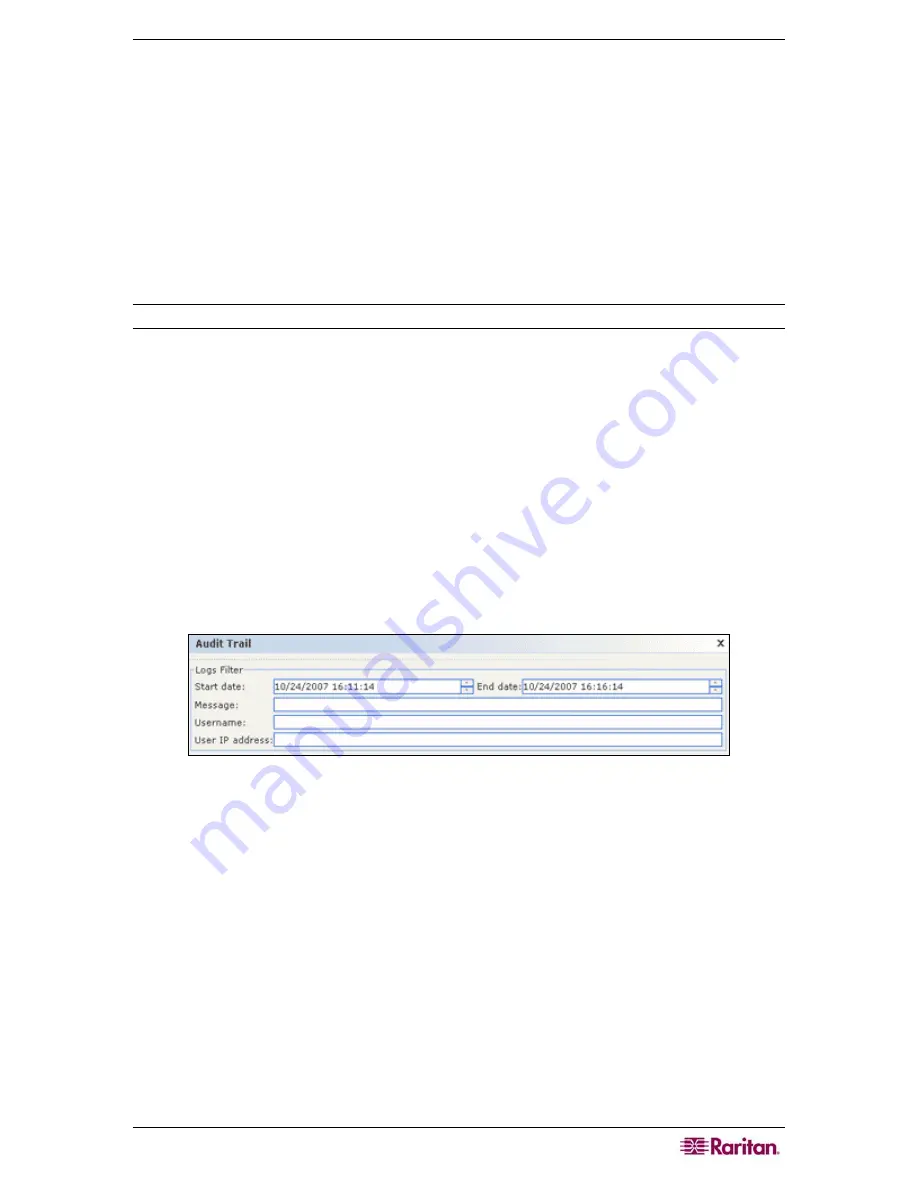
Figure 112 Audit Trail Screen
2.
Set the date range for the report in the
Start Date
and
End Date
fields. Click each
component of the default date (month, day, year, hour, minute, second) to select it, and then
click the up and down arrows to reach the desired number.
3.
You can limit the data that the report will contain by entering additional parameters in the
Message
,
Username
, and
User
IP
address
fields.
•
If you want to limit the report by the message text associated with an activity, type the text in
the
Message
field.
•
If you want to limit the report to a particular user’s activities, type the user’s username in the
Username
field.
•
If you want to limit the report to a particular IP address’s activities, type the user’s IP address
in the
User IP address
field.
Summary of Contents for CC-SG
Page 2: ...This page intentionally left blank...
Page 26: ...12 COMMANDCENTER SECURE GATEWAY ADMINISTRATOR GUIDE This page intentionally left blank...
Page 46: ...32 COMMANDCENTER SECURE GATEWAY ADMINISTRATOR GUIDE This page intentionally left blank...
Page 158: ...144 COMMANDCENTER SECURE GATEWAY ADMINISTRATOR GUIDE This page intentionally left blank...
Page 228: ...214 COMMANDCENTER SECURE GATEWAY ADMINISTRATOR GUIDE This page intentionally left blank...
Page 236: ......
Page 246: ...232 COMMANDCENTER SECURE GATEWAY ADMINISTRATOR GUIDE...
Page 248: ...234 COMMANDCENTER SECURE GATEWAY ADMINISTRATOR GUIDE...
Page 250: ...236 COMMANDCENTER SECURE GATEWAY ADMINISTRATOR GUIDE...
Page 256: ...242 COMMANDCENTER SECURE GATEWAY ADMINISTRATOR GUIDE...
















































