Appendix B: CC-SG and Network Configuration
350
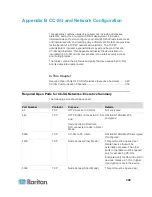
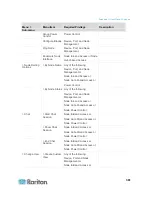
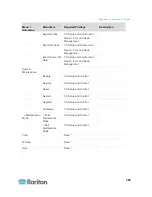
Port Number
Protocol
Purpose
Details
Raritan device that will be
externally accessed. The other
ports in the table must be opened
only for accessing CC-SG.
AES-128/AES-256 encrypted if
configured.
80 and 443 for Control
System nodes
80, 443, 902, and 903 for
Virtual Host and Virtual
Machine Nodes
TCP
Virtual Node Access
N/A
51000
TCP
SX Target Access (Direct
Mode)
AES-128/AES-256 encrypted if
configured.
Possible exceptions to the required open ports:
Port 80 can be closed if all access to the CC-SG is via HTTPS
addresses.
Ports 5000 and 51000 can be closed if CC-SG Proxy mode is used for
connections from the firewall.
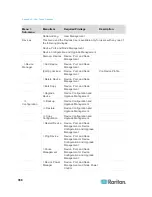
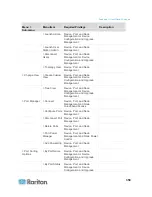
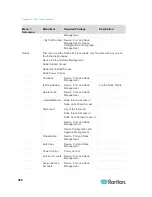
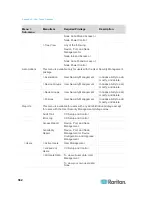
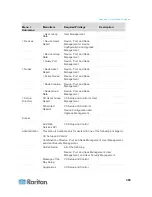
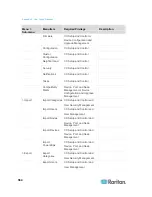
CC-SG Communication Channels
Each communication channel is documented. For each communication
channel, the table includes:
The symbolic IP Addresses used by the communicating parties.
These addresses must be allowed over any communication path
between the entities.
The Direction in which the communication is initiated. This may be
important for your particular site policies. For a given CC-SG role,
the path between the corresponding communicating parties must be
available and for any alternate re-route paths that might be used in
the case of a network outage.
The Port Number and Protocol used by CC-SG.
Whether the port is Configurable, which means the Admin Client or
Diagnostic Console provides a field where you can change the port
number to a different value from the default listed if there are
conflicts with other applications on the network or for security
reasons.
Details about the method of communication, the message that is
passed via the communication channel, or its encryption.