126
COMMANDCENTER NOC ADMINISTRATOR GUIDE
on demand. The remaining item is determining when performance metrics have reached a point at
which they should be acted upon. And with the CC-NOC’s capability of managing performance
thresholds, that’s easy too!
Thresholding
An exciting new feature significantly improved with the CC-NOC is threshold alerts. This
allows the CC-NOC to notify you of potential problems pro-actively, before they occur, based
on performance metrics gathered by the CC-NOC through SNMP and WMI.
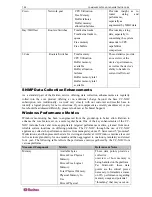
How it works
The CC-NOC gathers performance data directly from managed devices using SNMP, and
through a proxy system for Windows Servers, and 5 workstations, using a CC-NOC appliance.
Each time the data is collected or reported, the CC-NOC compares certain data points against
configurable
threshold
values. Click the
Admin
tab,
Network Management
,
Configure
Performance Thresholds
for details on how to configure thresholds. If the value is higher or
lower, depending on the type of threshold, than the threshold value, an event will be generated.
This event can be configured for notification through the notification configuration option under
the
Admin
tab.
There are four key pieces to threshold monitoring: type, value, trigger, and rearm.
Type
A threshold can be a high or low threshold. A high threshold means that an event will be
generated if the actual value is higher than the threshold value. Conversely, a low threshold will
cause an event to be generated when the actual value reported is lower than the threshold value.
Value
Value refers to the point at which the threshold is exceeded, whether it is a low or high threshold.
For instance, if the value for a high threshold is 80, any reported value over 80 will exceed the
threshold.
Trigger
The trigger is the number of times in a row the threshold must be exceeded before an event is
generated. If a trigger is set at 3, for example, the threshold must be exceeded for three
consecutive reports before an event is generated.
Rearm
After an event is generated, no further events will be generated for the same threshold until the
rearm value is reached. The rearm value protects you from a flurry of events when the value
bounces
around
the threshold value—just above and just below. The rearm value must be
reached in the
opposite
direction of the threshold type. For example, if a disk drive had a high
threshold of 90% utilization and no rearm value, an application that wrote a temporary file and
deleted it on exit might cause the utilization to bounce between 89% and 90%. The rearm value
protects you from this condition by enforcing that the utilization problem must be addressed, as
opposed to temporarily repaired. Until the utilization drops below 80%, you will not receive
another notification.
Summary of Contents for COMMANDCENTER NOC
Page 2: ...This page intentionally left blank...
Page 12: ...xii FIGURES...
Page 20: ...8 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Page 114: ...102 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Page 132: ...120 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Page 144: ...132 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Page 148: ...136 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Page 155: ...APPENDIX G NETWORK TRAFFIC OVERHEAD NETWORK MANAGEMENT S NECESSARY EVIL 143 255 80 5301 00...