Key Archival Process
Chapter 6
Data Recovery Manager
191
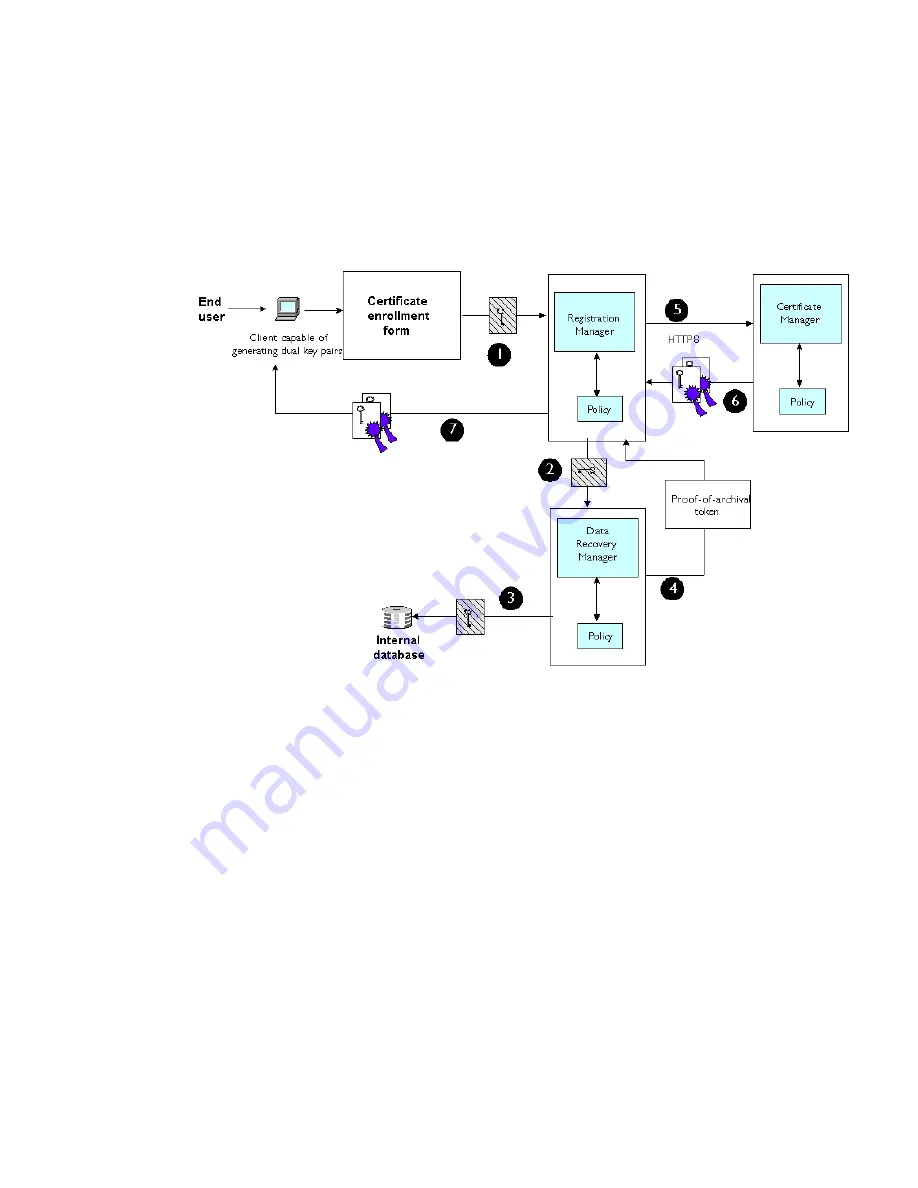
Figure 6-1 illustrates how the key archival process occurs when an end-entity’s requests a
certificate. The deployment scenario shown in this figure has a Registration Manager acting
as the trusted enrollment authority to a Certificate Manager and Data Recovery Manager.
Figure 6-1
How the key archival process works
These are the steps shown in Figure 6-1:
1.
A end entity uses a client capable of generating dual key pairs to access the certificate
enrollment form served by the Registration Manager, fills in all the information, and
submits the request.
The client detects the JavaScript option and exports only the end-entity’s encryption
private key, not the signing private key.
The Registration Manager detects the key archival option in the end-entity’s request
and asks the client for the end-entity’s encryption private key.
The client encrypts the end-entity’s encryption private key with the public key from the
Data Recovery Manager’s transport certificate; a copy of the transport certificate is
embedded in the enrollment form.
Summary of Contents for CERTIFICATE 7.1 ADMINISTRATOR
Page 1: ...Administrator s Guide Red Hat Certificate System Version7 1 September 2005 ...
Page 22: ...22 Red Hat Certificate System Administrator s Guide September 2005 ...
Page 128: ...Cloning a CA 128 Red Hat Certificate System Administrator s Guide September 2005 ...
Page 368: ...ACL Reference 368 Red Hat Certificate System Administrator s Guide September 2005 ...
Page 460: ...Constraints Reference 460 Red Hat Certificate System Administrator s Guide September 2005 ...
Page 592: ...CRL Extension Reference 592 Red Hat Certificate System Administrator s Guide September 2005 ...
















































