Chapter 15. Configuring Subsystem Logs
376
3. Start the TPS instance.
service pki-tps start
15.5. Managing Signed Audit Logs
The audit log contains records for events that have been set up as recordable events. If the
logSigning
attribute is set to
true
, the audit log is signed with a log signing certificate belonging to
the server. This certificate can be used by auditors to verify that the log has not been tampered with.
By default, regular audit logs are located in the
/var/log/
subsystem_name
directory with other
types of logs, while signed audit logs are written to
/var/log/
subsystem_name
/signedAudit/
.
The default location for logs can be changed by modifying the configuration.
15.5.1. Configuring a Signed Audit Log for a CA, OCSP, DRM, or
TKS
The signed audit log creates a log recording system events, and the events are selected from a list
of potential events. When enabled, signed audit logs record a verbose set of messages about the
selected event activity.
Signed audit logs are configured by default when the instance is first created, but it is possible to edit
the configuration or change the signing certificates after configuration.
TIP
Provide enough space in the filesystem for the signed audit logs, since they can be large.
NOTE
The audit logs for an RA subsystem cannot be signed. TPS audit log signing is described
in
Section 15.5.2, “Configuring TPS Signed Audit Logging”
.
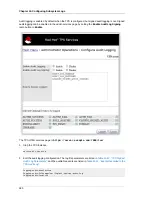
A log is set to a signed audit log by setting the
logSigning
parameter to
enable
and providing the
nickname of the certificate used to sign the log. A special log signing certificate is created when the
CA, DRM, OCSP, TKS, and TPS subsystems are first configured.
Only a user with auditor privileges can access and view a signed audit log. Auditors can use the
AuditVerify
tool to verify that signed audit logs have not been tampered with.
The signed audit log is created and enabled when the subsystem is configured, but it needs additional
configuration to begin creating and signing audit logs.
1. Open the Console.
NOTE
To create or configure the audit log by editing the
CS.cfg
file, see
Section 15.4,
“Configuring Logs in the CS.cfg File”
.
Summary of Contents for CERTIFICATE SYSTEM 8.0 - ADMINISTRATION
Page 42: ...20 ...
Page 43: ...Part I Setting up Certificate Services ...
Page 44: ......
Page 190: ...168 ...
Page 208: ...186 ...
Page 223: ...Part II Additional Configuration to Manage CA Services ...
Page 224: ......
Page 256: ...234 ...
Page 270: ...248 ...
Page 280: ...258 ...
Page 292: ...270 ...
Page 293: ...Part III Managing the Subsystem Instances ...
Page 294: ......
Page 408: ...386 ...
Page 438: ...416 ...
Page 439: ...Part IV References ...
Page 440: ......
Page 503: ...Netscape Defined Certificate Extensions Reference 481 OID 2 16 840 1 113730 13 ...
Page 504: ...482 ...
Page 556: ...534 ...
Page 564: ...542 ...