Chapter 1. Red Hat Cluster Suite Overview
25
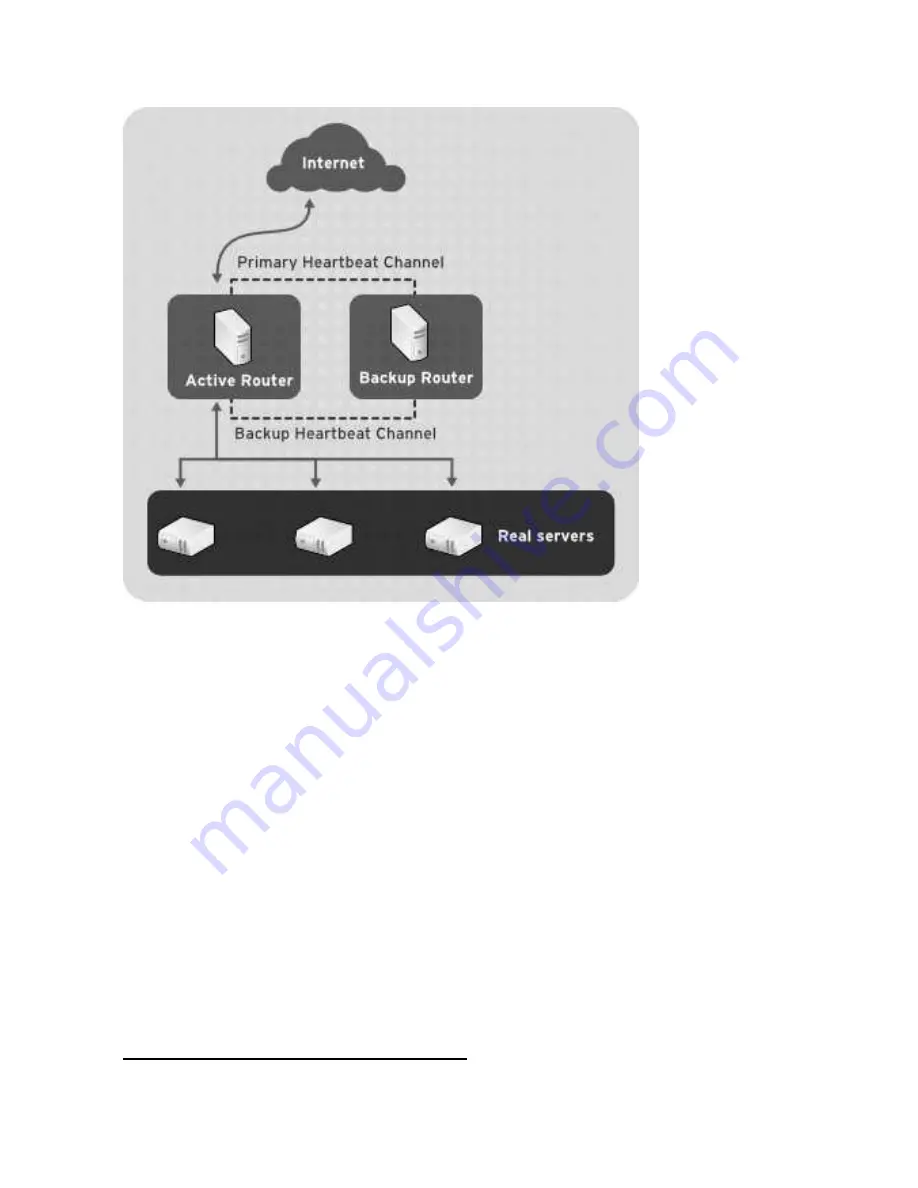
Figure 1-20. Two-Tier LVS Topology
Service requests arriving at an LVS router are addressed to a
virtual IP
address or VIP.
This is a publicly-routable address that the administrator of the site associates with a fully-
qualified domain name, such as www.example.com, and which is assigned to one or more
virtual servers
1
. Note that a VIP address migrates from one LVS router to the other during a
failover, thus maintaining a presence at that IP address, also known as
floating IP addresses
.
VIP addresses may be aliased to the same device that connects the LVS router to the public
network. For instance, if eth0 is connected to the Internet, then multiple virtual servers can
be aliased to
eth0:1
. Alternatively, each virtual server can be associated with a separate
device per service. For example, HTTP traffic can be handled on
eth0:1
, and FTP traffic
can be handled on
eth0:2
.
Only one LVS router is active at a time. The role of the active LVS router is to redirect
service requests from virtual IP addresses to the real servers. The redirection is based on
one of eight load-balancing algorithms:
•
Round-Robin Scheduling — Distributes each request sequentially around a pool of real
servers. Using this algorithm, all the real servers are treated as equals without regard to
capacity or load.
1. A virtual server is a service configured to listen on a specific virtual IP.
Summary of Contents for CLUSTER SUITE - FOR RHEL 4
Page 1: ...Red Hat Cluster Suite for RHEL 4 Overview ...
Page 4: ......
Page 10: ...vi About This Document ...
Page 47: ...Chapter 1 Red Hat Cluster Suite Overview 37 Figure 1 25 Cluster Configuration Structure ...
Page 62: ...52 Chapter 1 Red Hat Cluster Suite Overview ...
Page 72: ...62 Chapter 2 Red Hat Cluster Suite Component Summary ...
















































